Udated Real Questions for Microsoft 70-686 Exam 100% Exam Pass Promised By Braindump2go (171-180)
70-686 Exam Dumps Free Shared By Braindump2go For Instant Download Now! Download Latest 70-686 Exam Questions and pass 70-686 one time easily! Do you want to be a winner? Vendor: Microsoft
Exam Code: 70-686
Exam Name: Pro: Windows 7, Enterprise Desktop Administrator 
QUESTION 171
Your company uses Microsoft Windows Server Update Services (WSUS) to deploy software updates and service packs.
Microsoft releases a security update for Windows 7.
You have the following requirements:
- The security update must be deployed by 5:00 P.M. on Friday.
- Computers that are off when the security update is deployed must install the security update as soon as they are turned on.
You need to manage the software update process to meet the requirements.
What should you do? A. Approve the security update for installation through the WSUS console with no deadline.
B. Approve the security update for download through the WSUS console with a deadline of
Friday at 5:00 P.M.
C. Approve the security update for installation through the WSUS console with a deadline of
Friday at 5:00 P.M.
D. Approve the security update for download through the WSUS console with no deadline. Answer: C
Explanation:
Hints:
1. question mention at friday 5pm
2. question request install update in stead of download update QUESTION 172
You are the desktop architect for an enterprise organization with client computers that run Windows 7.
You need to create a new Windows Firewall rule that will allow you to access the Disk Management snap-in of remote client computers.
Which predefined rule should you select? To answer, select the appropriate setting in the work area. 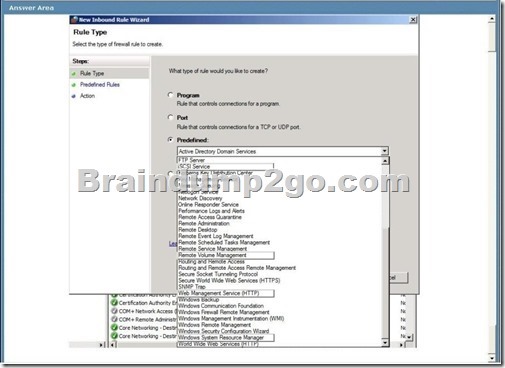
Answer: 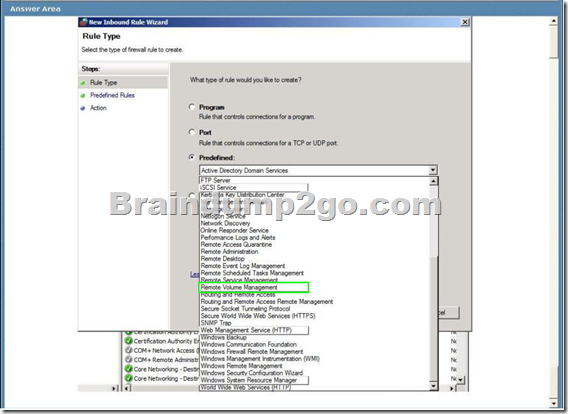
QUESTION 173
Your company has a single Active Directory Domain Services (AD DS) domain named
contoso.com that uses Active DirectoryCintegrated DNS.
You deploy the Key Management Service (KMS) on a Windows 7 computer.
You need to ensure that Windows 7 client computers can locate the KMS host and perform activation.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Create and deploy a GPO firewall rule to allow RPC traffic through TCP port 1688 on the
client computers.
B. Deploy a Windows Server 2008 KMS host.
C. Grant the KMS server the Full Control permission on the _vlmcs._tcp.contoso.com DNS
record.
D. Grant the KMS server the Full Control permission on the _msdcs._tcp.contoso.com DNS
zone. Answer: AC
Explanation:
http://technet.microsoft.com/en-us/library/ee939272.aspx 2 1
The KMS clients find the KMS host via a DNS SRV record (_vlmcs._tcp) and then automatically attempt to discover and use this service to activate themselves.
When in the 30 day Out of Box grace period, they will try to activate every 2 hours.
Once activated, the KMS clients will attempt a renewal every 7days.
Listening on Port:
Communication with KMS is via anonymous RPC.
1688 is the default TCP port used by the clients to connect to the KMS host.
Make sure this port is open between your KMS clients and the KMS host. QUESTION 174
Your network has 1,000 client computers that run Windows 7.
You need to install an application, in the Local System account context, on the client computers.
What are two possible ways to achieve this goal? (Each correct answer presents a complete
solution. Choose two.) A. Configure a logon script.
B. Configure a startup script.
C. Configure a shutdown script.
D. Configure a logoff script. Answer: BC QUESTION 175
Your company has two network segments.
The core network segment is where centralized management is performed.
The high-security network segment is an isolated network.
A firewall between the core network segment and the high-security network segment limits network communication between the segments.
These network segments are shown in the following diagram.
Your company plans to deploy Windows 7 to all client computers.
You need to manage activation for client computers that are located in the high-security network segment.
What should you do? 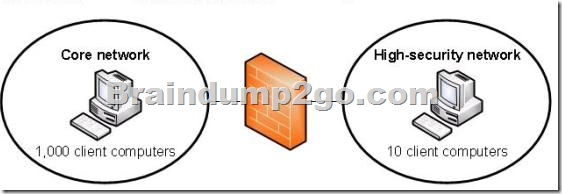
A. Deploy the Key Management Service (KMS) in the core network segment.
B. Deploy the Key Management Service (KMS) in the high-security network segment.
C. Install the Volume Activation Management Tool (VAMT) in the core network segment.
D. Install the Volume Activation Management Tool (VAMT) in the high-security network segment.
Answer: D
Explanation:
Key Management Service (KMS) requires a count of 25 or higher from the KMS host to activate itself.
Refer to http://technet.microsoft.com/en-us/library/ee939272.aspx 2 1
There is a firewall blocking, (VAMT) should setup at high-security network. QUESTION 176
Your company has client computers that run Windows XP Professional.
You are planning to install Windows 7 Enterprise on the existing client computers.
You need to ensure that the user state can be viewed after it has been collected and saved.
What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.) A. Perform an offline migration by using Windows PE.
B. Use an uncompressed migration store.
C. Perform an offline migration by using Windows.old.
D. Use a hard-link migration store. Answer: BD QUESTION 177
You plan to deploy Windows 7 to client computers.
You have the following requirements:
- Deploy Windows 7 over the network.
- Do not affect the performance of existing network applications.
You need to design a zero-touch deployment strategy that supports the requirements.
What should you do? A. Deploy images from a Microsoft System Center Configuration Manager server that runs
Windows Server 2008.
B. Deploy images from a dedicated share on a Windows Server 2008 server.
C. Ensure that all computers have the Internet Protocol version 6 (IPv6) protocol disabled prior
to deployment
D. Ensure that all computers have the Internet Protocol version 4 (IPv4) protocol disabled prior
to deployment. Answer: A QUESTION 178
Your company has an Active Directory Domain Services (AD DS) forest with a single domain.
A server has the Windows Deployment Services (WDS) role installed.
You create a Windows 7 image.
You plan to use the Lite Touch Installation deployment method to deploy the Windows 7 image.
You need to design a deployment strategy that will install an image on unknown client computers only if administrative approval is granted.
What should you do? A. Create a multicast transmission for the Windows 7 image.
B. Use an Auto-Add policy on the WDS server.
C. Create a unicast transmission for the Windows 7 image.
D. Use DHCP rogue detection on the WDS server. Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/cc731409(v=ws.10).aspx#BKMK_2 3 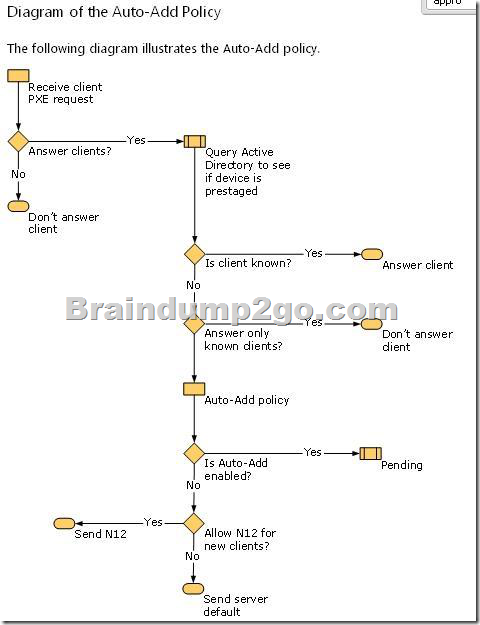
untitled QUESTION 179
Your network has 1,000 client computers that run Windows XP.
You are planning to deploy Windows 7.
You plan to use the Microsoft Deployment Toolkit Lite Touch Installation deployment method to deploy the Windows 7 image.
You have the following requirements:
- Migrate 20 computers at a time.
- Ensure that you conserve network bandwidth.
You need to design a deployment strategy that meets the requirements.
What should you do? A. Configure multicast transmission on the deployment point.
B. Configure unicast transmission on the deployment point.
C. Distribute the image by using Background Intelligent Transfer Service (BITS).
D. Compress the contents of the distribution folder. Answer: A
Explanation:
Performing Multicast Deployments
In order to deploy an image using multicasting instead of unicasting, you must first create a multicast transmission. Multicast transmissions make the image available for multicasting, which enables you to deploy an image to a large number of client computers without overburdening the network. When you deploy an image using multicasting, the image is sent over the network only once, which can drastically reduce the amount of network bandwidth that is used.
http://technet.microsoft.com/en-us/library/dd637994(v=ws.10).aspx 4 QUESTION 180
Your company has a single Active Directory Domain Services (AD DS) domain and 1,000 client computers.
You are planning to deploy Windows 7 by using a zero-touch installation process.
You need to test the deployment methodology.
What should you do first? A. Create a computer collection with test computers as members.
B. Create a security group with test computers as members.
C. Create an organizational unit and move test computer accounts into it.
D. Create a distribution group with test computers as members. Answer: A
Instant Download Braindump2go New Released Microsoft 70-686 Exam Dumps PDF & VCE! Enjoy 1 year Free Updation! 100% Exam Pass Guaranteed Or Full Money Back! 
http://www.braindump2go.com/70-686.html
|





