[Sep-2019-New]Braindump2go 400-251 Exam Dumps PDF Free Instant Download(New Questions)
August/2019 Braindump2go 400-251 Exam Dumps with PDF and VCE New Updated Today! Following are some 400-251 Real Exam Questions:
1.|2019 Latest Braindump2go 400-251 Exam Dumps (PDF & VCE) Instant Download: https://www.braindump2go.com/400-251.html 2.|2019 Latest Braindump2go 400-251 Exam Questions & Answers Instant Download: https://drive.google.com/drive/folders/0B75b5xYLjSSNcGJLWWtfdE96ZUU?usp=sharing New Questions
Refer to the exhibit. Which effect of this command is true?
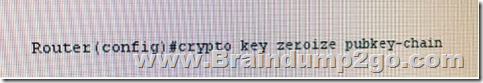 A. The current public key of the router is deleted from the cache when the router reboots, and the router generates a new one. A. The current public key of the router is deleted from the cache when the router reboots, and the router generates a new one.
B. The CA revokes the public key certificate of the router.
C. The public key of the remote peer is deleted from the router cache.
D. The router immediately deletes its current public key from the cache and generates a new one.
E. The router sends a request to the CA to delete the router certificate from its configuration.
Answer: C New Questions
Refer to the exhibit. If you apply the given command to a Cisco device running IOS or IOS XE, which two statements about connections to the HTTP server on the device are true?(Choose two)
 A. The device will close each connection after 90 seconds even if a connection is actively processing a request.
B. Connections will close after 60 seconds without activity or 90 seconds with activity.
C. Connections will close after 60 seconds or as soon as the first request is processed.
D. When you apply the command , the device will immediately close any existing connections that have been open for longer than 90 seconds.
E. Connections will close after 60 seconds without activity or as soon as the first request is processed. Answer: BE
Explanation:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/https/configuration/12-2sy/https-12-2sy-book/nm-http-web.html New Questions
Which two statements about global ACLs are true? (Choose two) A. They support an implicit deny
B. They are applied globally instead of being replicated on each interface
C. They override individual interface access rules
D. They require an explicit deny
E. They can filer different packet types than extended ACLs
F. They require class-map configuration Answer: AB New Questions
What are two security controls you can implement to protect your organization's network from virus and worm outbreak? (Choose two) A. Require users to authenticate before accessing the network
B. Quarantine hosts that fail to meet your organization's IT security requirements
C. Implement Cisco identity service Engine (ISE. for network security
D. Implement routing protocols with strong interface authentication
E. Deploy Cisco prime LMS to manage network security Answer: BC New Questions
Which two statement about DHCP snooping are true? (Choose two) A. The binding database stores information about trusted interface.
B. Massages sent from outside the service-provider network are untrusted.
C. The binding database stores information about both IP and MAC addresses.
D. The lease time in the binding database is a pre-set value.
E. DHCP servers connect to untrusted interface on the switch. Answer: CD New Questions
Which command is required for bonnet filter on Cisco aASA to function properly? A. dynamic-filter inspect tcp/80
B. dynamic-filter whitelist
C. inspect botnet
D. inspect dns dynamic-filter-snoop Answer: D New Questions
What are three IPv6 extension headers? (Choose three) A. TTL
B. source option
C. Destination options
D. Authentication
E. Segment
F. Hop-by-Hop options Answer: CDF New Questions
What command specifies the peer from which MSDP SA message are accepted? A. IP msdpsa-filter in <peer>[list<acl>] [route-map <map> ]
B. Ipmsdp default-peer <peer>
C. Ipmsdp mesh-group
D. Ipmsdp originator-id <interface> Answer: B New Questions
Which two statements about the AES algorithm are true? (Choose two) A. The AES algorithm is an asymmetric block cipher.
B. The AES algorithm operates on a 128-bits block.
C. The AES algorithm uses a fixed length-key of 128 bits.
D. The AES algorithm does not give any advantage over 3DES due to the same key length.
E. The AES algorithm consist of four functions. Three functions provide confusion-diffusion and one provides encryption. Answer: BE New Questions
Which feature can prevent IP spoofing attacks? A. CoPP
B. CBAC
C. ARP spoofing
D. TCP Intercept
E. Unicast RPF
F. CAR Answer: E New Questions
What technique can an attacker use to obfuscate a malware application payload, allowing it to bypass standard security mechanisms? A. Teredo tunnelling
B. Decryption
C. A PE32 header
D. Steganography
E. BASE64 Answer: E
New Questions
What are three protocol that support layer 7 class maps and policy maps for zone based firewalls? (choose three) A. IMAP
B. RDP
C. MME
D. ICQ
E. POP3
F. IKE Answer: ADE New Questions
You have configured an authenticator switch in access mode on a network configured with NEAT what radius attribute must the ISE server return to change the switch's port mode to trunk? A. device-traffic-class=switch
B. device-traffic-class=trunk
C. framed-protocol=1
D. EAP-message-switch
E. Authenticate=Administrative
F. Acct-Authentic=radius Answer: A New Questions
Refer to the exhibit. Which statement about the router R1 is true? 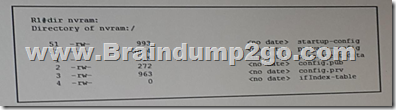 A. Its private-config is corrupt.
B. Its NVRAM contains public and private crypto keys.
C. Its running configuration is missing.
D. RMON is configured. Answer: B New Questions
Refer to the Exhibit. What is the effect of the given ACL policy ?
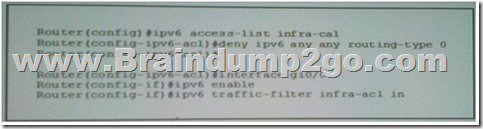 A. The policy will deny all IPv6 eBGP session.
B. The policy will disable IPv6 source routing.
C. The policy will deny all IPv6 routing packet.
D. The policy will deny all IPv6 routed packet. Answer: B New Questions
Which three statements about the RSA algorithm are true? (Choose three.) A. The RSA algorithm provides encryption but not authentication.
B. The RSA algorithm provides authentication but not encryption.
C. The RSA algorithm creates a pair of public-private keys that are shared by entities that perform encryption.
D. The private key is never sent across after it is generated.
E. The public key is used to decrypt the message that was encrypted by the private key.
F. The private key is used to decrypt the message that was encrypted by the public key. Answer: CDF New Questions
Which of these is a core function of the risk assessment process? (Choose one.) A. performing regular network upgrades
B. performing network optimization
C. performing network posture validation
D. establishing network baselines
E. prioritizing network roll-outs Answer: C New Questions
Which two router configurations block packets with the Type 0 Routing header on the interface? (Choose two) A. Ipv6 access-list Deny_Loose_Routing
permit ipv6 any any routing-type 0
deny ipv6 any any
interface FastEthernet0/0
ipv6 traffic-filter Deny_Loose_Source_Routing in
B. Ipv6 access-list-Deny_Loose_Source_Routing
Deny ipv6 FE80::/10 any mobility -type bind-refresh
Interface FastEthernet/0
Ipv6 tr
Affic-filter Deny_Loose_Source_Routing in
C. Ipv6 access-list Deny_Loose_Source_Routing
Deny ipv6 any any routing-type 0
Permit ipv6 any any
Interface FastEthernet0/0
Ipv6 traffic -filter Deny_Loose_Routing in
D. Ipv6 access -list Deny_Loose_Source_Routing
Deny ipv6 any FE80: :/10 routing -type 0
Deny ipv6 any any routing -type 0
Permit ipv6 any any
Interface FastEthernet t0/0
Ipv6 traffic -filter Deny_Loose_Source_Routing in
E. Ipv6 access -list Deny_Loose_Source_Routing
Sequence 1 deny ipv6 any any routing -type 0 log-input
Sequence 2 permit ipv6 any any flow -label 0 routing interface Fastethernet0/0
Ipv6 traffic-filter Deny_Loose_Source_Routing in Answer: CD New Questions
What protocol provides security for datagram protocols? A. MAB
B. DTLS
C. SCEP
D. GET
E. LDP Answer: B New Questions
Which two options are open-source SDN controllers? (Choose two) A. OpenContrail
B. OpenDaylight
C. Big Cloud Fabric
D. Virtual Application Networks SDN Controller
E. Application Policy Infrastructure Controller Answer: AB New Questions
Which current RFC made RFCs 2409, 2407, and 2408 obsolete? A. RFC 4306
B. RFC 2401
C. RFC 5996
D. RFC 4301
E. RFC 1825 Answer: A New Questions
Refer to the exhibit. Which effect of this configuration is true?
 A. It enables MLD query messages for all link-local groups.
B. It configures the node to generate a link-local group report when it joins the solicited- node multicast group.
C. It enables hosts to send MLD report messages for groups 224.0.0.0/24.
D. it enables local group membership for MLDv1 and MLDv2.
E. It enables the host to send MLD report messages for nonlink local groups. Answer: C New Questions
Which technology builds on the vPathconcept and can be used in virtual and physical environments? A. VXLAN
B. ACI
C. NSH
D. SDN Answer: C
!!!RECOMMEND!!!1.|2019 Latest Braindump2go 400-251 Exam Dumps (PDF & VCE) Instant Download: https://www.braindump2go.com/400-251.html 2.|2019 Latest Braindump2go 400-251 Study Guide Video Instant Download: YouTube Video: YouTube.com/watch?v=ZafUReZ2oxM 1
|

 A. The current public key of the router is deleted from the cache when the router reboots, and the router generates a new one.
A. The current public key of the router is deleted from the cache when the router reboots, and the router generates a new one.

