[OFFICIAL]Braindump2go 70-411 Dumps PDF Download (61-70)
MICROSOFT OFFICIAL: New Updated 70-411 Exam Questions from Braindump2go 70-411 PDF Dumps and 70-411 VCE Dumps! Welcome to Download the Newest Braindump2go 70-411 VCE&PDF Dumps: http://www.braindump2go.com/70-411.html (322 Q&As) We never believe in second chances and Braindump2go brings you the best 70-411 Exam Preparation Materials which will make you pass in the first attempt.We guarantee all questions and answers in our 70-411 Dumps are the latest released,we check all exam dumps questions from time to time according to Microsoft Official Center, in order to guarantee you can read the latest questions! Exam Code: 70-411
Exam Name Administering Windows Server 2012
Certification Provider: Microsoft
Corresponding Certifications: MCSA, MCSA: Windows Server 2012, MCSE, MCSE: Desktop Infrastructure, MCSE: Private Cloud, MCSE: Server Infrastructure Keywords:70-411 Dumps,70-411 Microsoft Exam Questions,70-411 VCE,70-411 PDF,70-411 Practice Exams,70-411 Practice Tests,70-411 Book,70-411 Study Guide 
QUESTION 61
Hotspot Question
Your network contains an Active Directory named contoso.com.
You have users named User1 and user2.
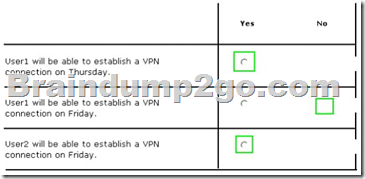
The Network Access Permission for User1 is set to Control access through NPS Network Policy. The Network Access Permission for User2 is set to Allow access.
A policy named Policy1 is shown in the Policy1 exhibit. (Click the Exhibit button.) 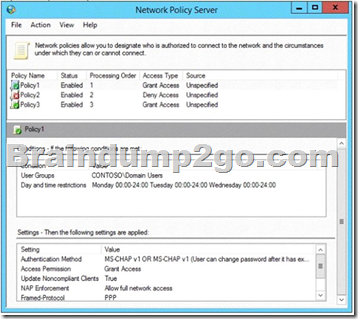
A policy named Policy2 is shown in the Policy2 exhibit. (Click the Exhibit button.) 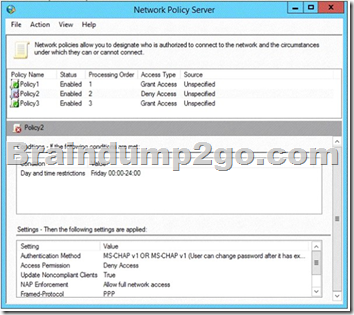
A policy named Policy3 is shown in the Policy3 exhibit. (Click the Exhibit button.) 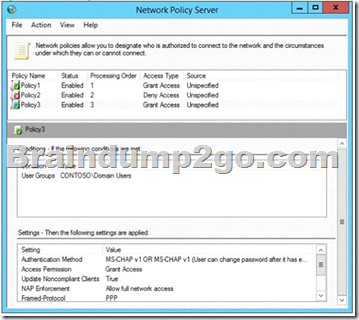
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point. 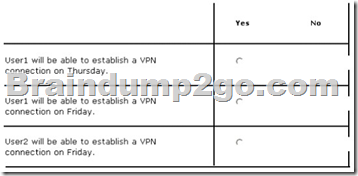
Answer:
QUESTION 62
Drag and Drop Question
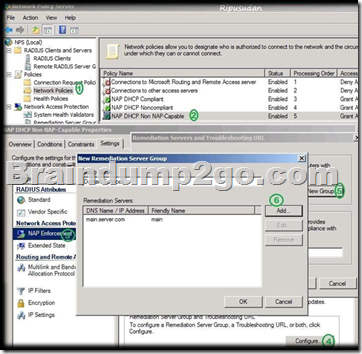
Your network contains an Active Directory domain named adatum.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 is configured as a Network Policy Server (NPS) server and as a DHCP server.
You need to log all DHCP clients that have windows Firewall disabled.
Which three actions should you perform in sequence?
To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
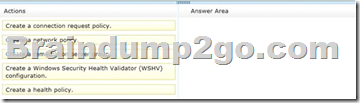
Answer: 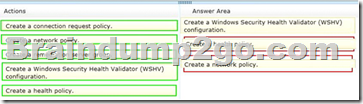
Explanation:
http://technet.microsoft.com/es-es/library/dd314198%28v=ws.10%29.aspx
http://technet.microsoft.com/es-es/magazine/2009.05.goat.aspx
http://technet.microsoft.com/es-es/library/dd314173%28v=ws.10%29.aspx
http://ripusudan.wordpress.com/2013/03/19/how-to-configure-nap-enforcement-for-dhcp/ http://technet.microsoft.com/es-es/magazine/2009.05.goat.aspx
http://technet.microsoft.com/en-us/library/dd125379%28v=ws.10%29.aspx http://technet.microsoft.com/en-us/library/cc772356%28v=ws.10%29.aspx 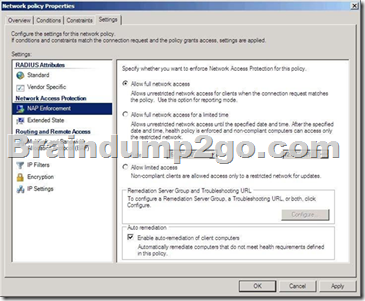
QUESTION 63
Your network contains an Active Directory domain named contoso.com.
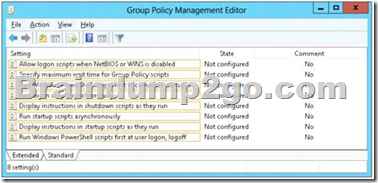
You have several Windows PowerShell scripts that execute when client computers start. When a client computer starts, you discover that it takes a long time before users are prompted to log on.
You need to reduce the amount of time it takes for the client computers to start. The solution must not prevent scripts from completing successfully.
Which setting should you configure? To answer, select the appropriate setting in the answer area.
Answer: 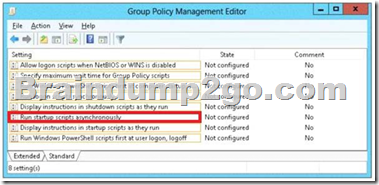
Explanation:
Lets the system run startup scripts simultaneously rather than waiting for each to finish http://technet.microsoft.com/en-us/library/cc939423.aspx QUESTION 64
Drag and Drop Question
You are a network administrator of an Active Directory domain named contoso.com.
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Web Server (IIS) server role installed. Server1 will host a web site at URL https:// secure.contoso.com. The application pool identity account of the web site will be set to a domain user account named AppPool1.
You need to identify the setspn.exe command that you must run to configure the appropriate Service Principal Name (SPN) for the web site.
What should you run? To answer, drag the appropriate objects to the correct location. Each object may be used once, more than once, or not at all. 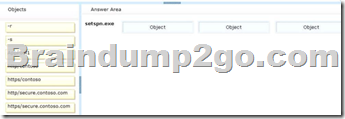
Answer: 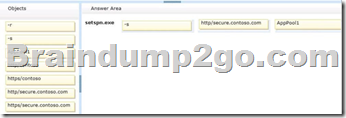
Explanation:
Note:
* -s <SPN>
Adds the specified SPN for the computer, after verifying that no duplicates exist.
Usage: setspn -s SPN accountname
For example, to register SPN "http/daserver" for computer "daserver1":
setspn -S http/daserver daserver1
http://technet.microsoft.com/en-us/library/cc731241(v=ws.10).aspx QUESTION 65
Your network contains a server named Server1 that has the Network Policy and Access Services server role installed.
All of the network access servers forward connection requests to Server1.
You create a new network policy on Server1.
You need to ensure that the new policy applies only to connection requests from the
192.168.0.0/24 subnet.
What should you do? A. Set the Client IP4 Address condition to 192.168.0.0/24.
B. Set the Client IP4 Address condition to 192.168.0.
C. Set the Called Station ID constraint to 192.168.0.0/24.
D. Set the Called Station ID constraint to 192.168.0. Answer: B
Explanation:
Called Station ID condition specifies the network access server telephone number dialed by access client.
Client IPv4 Address condition specifies the Internet Protocol (IP) version 4 address of the RADIUS client that forwarded the connection request to the NPS server. QUESTION 66
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains 500 client computers that run Windows 8 Enterprise.
You implement a Group Policy central store.
You have an application named Appl. Appl requires that a custom registry setting be deployed to all of the computers.
You need to deploy the custom registry setting. The solution must minimize administrator effort.
What should you configure in a Group Policy object (GPO)? A. The Administrative Templates
B. An application control policy
C. The Group Policy preferences
D. Software installation setting Answer: C
Explanation:
Group Policy preferences provide the means to simplify deployment and standardize configurations. They add to Group Policy a centralized system for deploying preferences (that is, settings that users can change later).
You can also use Group Policy preferences to configure applications that are not Group Policy- aware. By using Group Policy preferences, you can change or delete almost any registry setting, file or folder, shortcut, and more.
You are not limited by the contents of Administrative Template files.
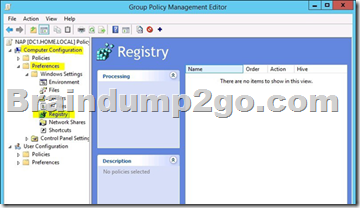
The Group Policy Management Editor (GPME) includes Group Policy preferences.
http://technet.microsoft.com/en-us/library/gg699429.aspx
http://www.unidesk.com/blog/gpos-set-custom-registry-entries-virtual-desktops-disabling-machine-password 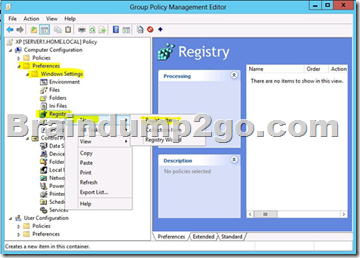
QUESTION 67
Your network contains an Active Directory domain named contoso.com. The domain contains a server named NPS1 that has the Network Policy Server server role installed. All servers run Windows Server 2012 R2.
You install the Remote Access server role on 10 servers.
You need to ensure that all of the Remote Access servers use the same network policies.
Which two actions should you perform?
(Each correct answer presents part of the solution.
Choose two.)
A. Configure each Remote Access server to use the Routing and Remote Access service (RRAS) to authenticate connection requests.
B. On NPS1, create a remote RADIUS server group.
Add all of the Remote Access servers to the remote RADIUS server group.
C. On NPS1, create a new connection request policy and add a Tunnel-Type and a Service-Type condition.
D. Configure each Remote Access server to use a RADIUS server named NPS1.
E. On NPS1, create a RADIUS client template and use the template to create RADIUS clients. Answer: CD
Explanation:
Connection request policies are sets of conditions and settings that allow network administrators to designate which RADIUS servers perform the authentication and authorization of connection requests that the server running Network Policy Server (NPS) receives from RADIUS clients. Connection request policies can be configured to designate which RADIUS servers are used for RADIUS accounting.
When you configure Network Policy Server (NPS) as a Remote Authentication Dial-In User Service (RADIUS) proxy, you use NPS to forward connection requests to RADIUS servers that are capable of processing the connection requests because they can perform authentication and authorization in the domain where the user or computer account is located. For example, if you want to forward connection requests to one or more RADIUS servers in untrusted domains, you can configure NPS as a RADIUS proxy to forward the requests to the remote RADIUS servers in the untrusted domain.
To configure NPS as a RADIUS proxy, you must create a connection request policy that contains all of the information required for NPS to evaluate which messages to forward and where to send the messages.
http://technet.microsoft.com/en-us/library/cc730866(v=ws.10).aspx QUESTION 68
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2.
You create an Active Directory snapshot of DC1 each day.
You need to view the contents of an Active Directory snapshot from two days ago.
What should you do first? A. Run the dsamain.exe command.
B. Stop the Active Directory Domain Services (AD DS) service.
C. Run the ntdsutil.exe command.
D. Start the Volume Shadow Copy Service (VSS). Answer: C
Explanation:
After you create and mount a snapshot, you can run Dsamain.exe to expose the AD DS or AD LDS data in the snapshot
https://technet.microsoft.com/en-us/library/cc753609(v=ws.10).aspx
ntdsutil first
dsamain after QUESTION 69
Your network contains an Active Directory domain named adatum.com. All domain controllers run Windows Server 2012 R2. The domain contains a virtual machine named DC2.
On DC2, you run Get-ADDCCloningExcludedApplicationList and receive the output shown in the following table. 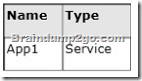
You need to ensure that you can clone DC2.
Which two actions should you perform?
(Each correct answer presents part of the solution. Choose two.) 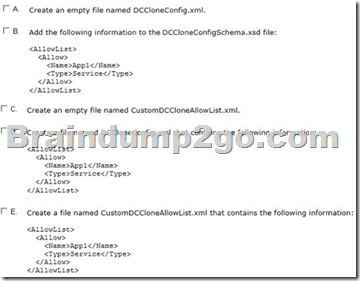
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
Answer: AE
Explanation:
Because domain controllers provide a distributed environment, you could not safely clone an Active Directory domain controller in the past.
Before, if you cloned any server, the server would end up with the same domain or forest, which is unsupported with the same domain or forest. You would then have to run sysprep, which would remove the unique security information before cloning and then promote a domain controller manually. When you clone a domain controller, you perform safe cloning, which a cloned domain controller automatically runs a subset of the sysprep process and promotes the server to a domain controller automatically.
The four primary steps to deploy a cloned virtualized domain controller are as follows:
- Grant the source virtualized domain controller the permission to be cloned by adding the source virtualized domain controller to the Cloneable Domain Controllers group.
- Run Get-ADDCCloningExcludedApplicationListcmdlet in Windows PowerShell to determine which services and applications on the domain controller are not compatible with the cloning.
- Run New-ADDCCloneConfigFile to create the clone configuration file, which is stored in the C:WindowsNTDS.
- In Hyper-V, export and then import the virtual machine of the source domain controller.
Run Get-ADDCCloningExcludedApplicationListcmdlet In this procedure, run the Get- ADDCCloningExcludedApplicationListcmdlet on the source virtualized domain controller to identify any programs or services that are not evaluated for cloning. You need to run the Get- ADDCCloningExcludedApplicationListcmdlet before the New- ADDCCloneConfigFilecmdlet because if the New- ADDCCloneConfigFilecmdlet detects an excluded application, it will not create a DCCloneConfig.xml file. To identify applications or services that run on a source domain controller which have not been evaluated for cloning
Get-ADDCCloningExcludedApplicationList
Get-ADDCCloningExcludedApplicationList -GenerateXml
The clone domain controller will be located in the same site as the source domain controller unless a different site is specified in the DCCloneConfig.xml file.
Note:
The Get-ADDCCloningExcludedApplicationListcmdlet searches the local domain controller for programs and services in the installed programs database, the services control manager that are not specified in the default and user defined inclusion list. The applications in the resulting list can be added to the user defined exclusion list if they are determined to support cloning. If the applications are not cloneable, they should be removed from the source domain controller before the clone media is created. Any application that appears in cmdlet output and is not included in the user defined inclusion list will force cloning to fail. The Get-ADDCCloningExcludedApplicationListcmdlet needs to be run before the New- ADDCCloneConfigFilecmdlet is used because if the New-ADDCCloneConfigFilecmdlet detects an excluded application, it will not create a DCCloneConfig.xml file.
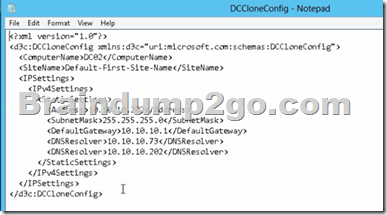
DCCloneConfig.xml is an XML configuration file that contains all of the settings the cloned DC will take when it boots. This includes network settings, DNS, WINS, AD site name, new DC name and more. This file can be generated in a few different ways.
The New-ADDCCloneConfigcmdlet in PowerShell
By hand with an XML editor
By editing an existing config file, again with an XML editor (Notepad is not an XML editor.) 
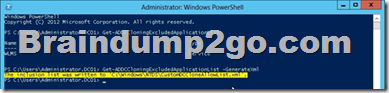
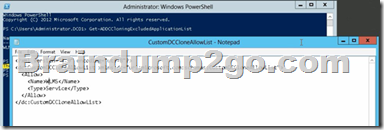
You can populate the XML file.....doesn't need to be empty..... 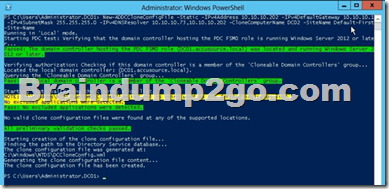
http://technet.microsoft.com/en-us/library/hh831734.aspx
http://blogs.dirteam.com/blogs/sanderberkouwer/archive/2012/09/10/new-features-in-active-directory-domain-services-in-windows-server-2012-part-13-domain-controller-cloning.aspx QUESTION 70
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You implement DirectAccess.
You need to view the properties of the DirectAccess connection.
Which connection properties should you view?
To answer, select the appropriate connection properties in the answer area. 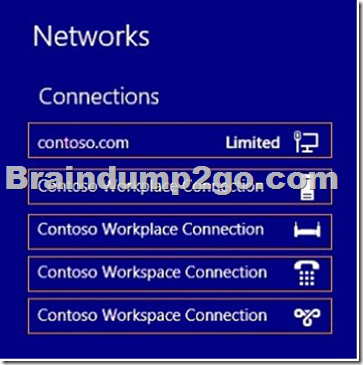
Answer: 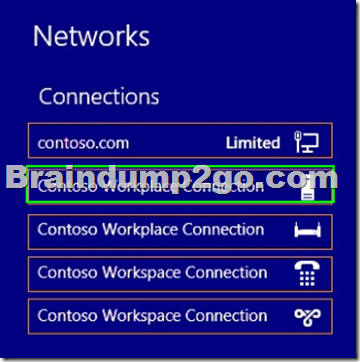
Explanation:
http://technet.microsoft.com/en-us/library/jj613767.aspx 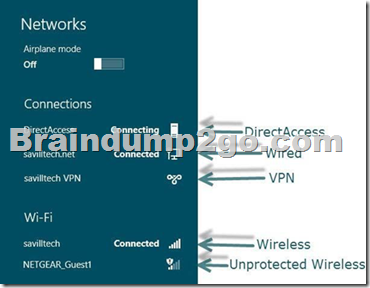
Braindump2go is one of the Leading 70-411 Exam Preparation Material Providers Around the World! We Offer 100% Money Back Guarantee on All Products! Feel Free In Downloading Our New Released 70-411 Real Exam Questions! 
FREE DOWNLOAD: NEW UPDATED 70-411 PDF Dumps & VCE Dumps from Braindump2go: http://www.braindump2go.com/70-411.html (322 Q&As)
|


























