[New-Sep.-2016]Valid Braindump2go Microsoft 70-410 PDF Questions and Answers 485q Offer[NQ31-NQ36]
2016/09 New Microsoft 70-410: Installing and Configuring Windows Server 2012 R2 Exam Questions Updated Today!
Free Instant Download 70-410 Exam Dumps (PDF & VCE) 485Q&As from Braindump2go.com Today! 100% Real Exam Questions! 100% Exam Pass Guaranteed!
1.|2016/09 Latest Microsoft 70-410 Exam Dumps (PDF & VCE) 485Q&As Download:
http://www.braindump2go.com/70-410.html
2.|2016/09 Latest Microsoft 70-410 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B75b5xYLjSSNfjBSYTlYY1lpNFI3MmhuSGFGVWtsT3RfTjRUcjd1NTlnNUJXbnMzajJ1Q0U&usp=sharing QUESTION 31
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 that runs Windows Server 2012 R2.
You need to configure a central store for the Group Policy Administrative Templates.
What should you do on DC1? A. From Server Manager, create a storage pool.
B. From Windows Explorer, copy the PolicyDefinitions folder to the SYSVOLcontoso.compolicies folder.
C. From Server Manager, add the Group Policy Management feature
D. From Windows Explorer, copy the PolicyDefinitions folder to the NETLOGON share. Answer: B
Explanation:
A. Create Disk Storage Pool
B. PolicyDefinitions folder in SYSVOL
C. Group Policy Management is a console for GPO Mgmt
D. Folder is for logon scripts
PolicyDefinitions folder within the SYSVOL folder hierarchy. By placing the ADMX files in this directory,they are replicated to every DC in the domain; by extension, the ADMX-aware Group Policy ManagementConsole in Windows Vista, Windows 7, Windows Server 2008 and R2 can check this folder as an additionalsource of ADMX files, and will report them accordingly when setting your policies.
By default, the folder is not created. Whether you are a single DC or several thousand, I would stronglyrecommend you create a Central Store and start using it for all your ADMX file storage. It really does work well.
The Central Store To take advantage of the benefits of .admx files, you must create a Central Store in the SYSVOL folder ona domain controller. The Central Store is a file location that is checked by the Group Policy tools. The GroupPolicy tools use any .admx files that are in the Central Store. The files that are in the Central Store are laterreplicated to all domain controllers in the domain. To create a Central Store for .admx and .adml files, create a folder that is named PolicyDefinitions in thefollowing location:
\FQDNSYSVOLFQDNpolicies
Note: FQDN is a fully qualified domain name.
http://tigermatt.wordpress.com/tag/policydefinitions/
http://support.microsoft.com/kb/929841/en-us
http://www.virtuallyimpossible.co.uk/how-to-create-a-group-policy-central-store/ http://support.microsoft.com/kb/2741591/en-us QUESTION 32
You install Windows Server 2012 R2 on a standalone server named Server1.
You configure Server1 as a VPN server.
You need to ensure that client computers can establish PPTP connections to Server1.
Which two firewall rules should you create? (Each correct answer presents part of the solution. Choose two.) A. An inbound rule for protocol 47
B. An outbound rule for protocol 47
C. An inbound rule for TCP port 1723
D. An inbound rule for TCP port 1701
E. An outbound rule for TCP port 1723
F. An outbound rule for TCP port 1701 Answer: AC
Explanation:
To enable VPN tunnels between individual host computers or entire networks that have a firewall between them, you must open the following ports:
PPTP
To allow PPTP tunnel maintenance traffic, open TCP 1723. To allow PPTP tunneled data to pass through router, open Protocol ID 47. http://www.windowsitpro.com/article/pptp/which-ports-do-you-need-to-open-on-a-firewall-to- allow-pptp-andl2tp-over-ipsec-vpn-tunnels--46811
If you use a personal firewall or a broadband router, or if there are routers or firewalls between the VPN client and the VPN server, the following ports and protocol must be enabled for PPTP on all firewalls and routers that are between the VPN client and the VPN server:
Client ports Server port Protocol
1024-65535/TCP 1723/TCP PPTP
Additionally, you must enable IP PROTOCOL 47 (GRE).
http://support.microsoft.com/kb/314076/en-us QUESTION 33
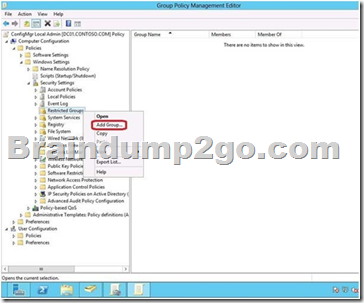
Your network contains an Active Directory domain named adatum.com. The computer accounts for all member servers are located in an organizational unit (OU) named Servers.
You link a Group Policy object (GPO) to the Servers OU.
You need to ensure that the domain's Backup Operators group is a member of the local Backup Operators group on each member server.
The solution must not remove any groups from the local Backup Operators groups.
What should you do? A. Add a restricted group named adatumBackup Operators.
Add Backup Operators to the This group is a member of list.
B. Add a restricted group named adatumBackup Operators.
Add Backup Operators to the Members of this group list.
C. Add a restricted group named Backup Operators.
Add adatumBackup Operators to the This group is a member of list.
D. Add a restricted group named Backup Operators.
Add adatumBackup Operators to the Members of this group list. Answer: A
Explanation:
A. The Member Of list specifies which other groups the restricted group should belong to
B. Needs to be added to member of list
C. Wrong group
D. Wrong group
Restricted groups allow an administrator to define two properties for security-sensitive groups (that is,"restricted" groups).
The two properties are Members and Member Of . The Members list defines who should and should not belongto the restricted group. The Member Of list specifies which other groups the restricted group should belong to.
When a restricted Group Policy is enforced, any current member of a restricted group that is not on theMembers list is removed. Any user on the Members list which is not currently a member of the restrictedgroup is added.
The Restricted Groups folder is available only in Group Policy objects associated with domains, OUs,and sites. The Restricted Groups folder does not appear in the Local Computer Policy object. If a Restricted Group is defined such that it has no members (that is, the Members list is empty), then allmembers of the group are removed when the policy is enforced on the system. If the Member Of list is emptyno changes are made to any groups that the restricted group belongs to. In short, an empty Members listmeans the restricted group should have no members while an empty Member Of list means "don't care" whatgroups the restricted group belongs to.
http://technet.microsoft.com/en-us/library/cc957640.aspx QUESTION 34
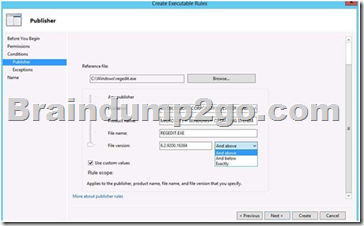
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. An application named Appl.exe is installed on all client computers. Multiple versions of Appl.exe are installed on different client computers. Appl.exe is digitally signed.
You need to ensure that only the latest version of Appl.exe can run on the client computers.
What should you create? A. An application control policy packaged app rule
B. A software restriction policy certificate rule
C. An application control policy Windows Installer rule
D. An application control policy executable rule Answer: D
Explanation:
A. A publisher rule for a Packaged app is based on publisher, name and version
B. You can create a certificate rule that identifies software and then allows or does not allow the software torun, depending on the security level.
C. For .msi or .msp
D. Executable Rules, for .exe and can be based on Publisher, Product name, filename and version. Use Certificate Rules on Windows Executables for Software Restriction Policies This security setting determines if digital certificates are processed when a user or process attempts to runsoftware with an .exe file name extension. This security settings is used to enable or disable certificate rules, atype of software restriction policies rule. With software restriction policies, you can create a certificate rule thatwill allow or disallow software that is signed by Authenticode to run, based on the digital certificate that isassociated with the software. In order for certificate rules to take effect, you must enable this security setting. When certificate rules are enabled, software restriction policies will check a certificate revocation list (CRL) tomake sure the software's certificate and signature are valid. This may decrease performance when start signedprograms. You can disable this feature. On Trusted Publishers Properties, clear the Publisher and Timestampcheck boxes.
http://technet.microsoft.com/en-us/library/dd759068.aspx
http://technet.microsoft.com/en-us/library/hh994588.aspx http://www.grouppolicy.biz/2012/08/how-manage-published-a-k-a-metro-apps-in-windows8-using- grouppolicy/
http://technet.microsoft.com/en-us/library/hh994597.aspx#BKMK_Cert_Rules http://technet.microsoft.com/en-us/library/cc782660%28v=ws.10%29.aspx QUESTION 35
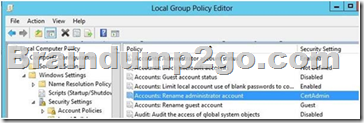
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2.
You need to ensure that the local Administrator account on all computers is renamed to L_Admin. Which Group Policy settings should you modify? A. Security Options
B. User Rights Assignment
C. Restricted Groups
D. Preferences Answer: A
Explanation:
A. Allows configuration of computers
B. User Rights Assignment policies determines which users or groups have logon rights or privileges on thecomputer
C. Restricted Groups defines what member or groups should exist as part of a group
D. With Preferences, local and domain accounts can be added to a local group without affecting the existingmembers of the group In Group Policy Object Editor, click Computer Configuration, click Windows Settings, click Security Settings,click Local Policies, and then click Security Options. In the details pane, double-click Accounts: Rename administrator account.
http://technet.microsoft.com/en-us/library/cc747484(v=ws.10).aspx
In Group Policy Object Editor, click Computer Configuration, click Windows Settings, click Security Settings, click Local Policies, and then click Security Options. In the details pane, double-click Accounts: Rename administrator account. QUESTION 36
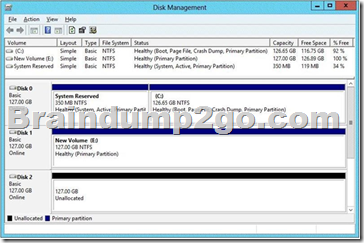
You have a server that runs Windows Server 2012 R2. The disks on the server are configured as shown in the exhibit. (Click the Exhibit button.)
You need to create a storage pool that contains Disk 1 and Disk 2.
What should you do first?
 A. Delete volume E
B. Convert Disk 1 and Disk 2 to dynamic disks
C. Convert Disk 1 and Disk 2 to GPT disks
D. Create a volume on Disk 2 Answer: A
Explanation:
A. Storage Pools use unallocated space
There is no way to create a storage pool with existing data.
Storage pools are only a collection ofdrives that are managed by windows.
http://technet.microsoft.com/en-us/library/ff399688.aspx
http://technet.microsoft.com/en-us/library/hh758075.aspx
!!!RECOMMEND!!! 1.|2016/09 Latest Microsoft 70-410 Exam Dumps (PDF & VCE) 485Q&As Download:
http://www.braindump2go.com/70-410.html
2.|2016/09 Latest Microsoft 70-410 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B75b5xYLjSSNfjBSYTlYY1lpNFI3MmhuSGFGVWtsT3RfTjRUcjd1NTlnNUJXbnMzajJ1Q0U&usp=sharing
|



