[New 300-209 Dumps]300-209 Free Dumps VCE Download from Braindump2go[371-381]
2018/September Braindump2go 300-209 Exam Dumps with PDF and VCE New Updated Today! Following are some new 300-209 Real Exam Questions:
1.|2018 Latest 300-209 Exam Dumps (PDF & VCE) 384Q&As Download: https://www.braindump2go.com/300-209.html
2.|2018 Latest 300-209 Exam Questions & Answers Download: https://drive.google.com/drive/folders/0B75b5xYLjSSNRkY3M21SbTdTNDg?usp=sharing QUESTION 371
An engineer is troubleshooting network issues and wants to check the Layer 2 connectivity between routers. Which command must be run? A. show ip eigrp neighbors
B. show cdp neighbor
C. show crypto isakmp sa.
D. show crypto issec sa. Answer: B QUESTION 372
Witch option is an advantage of using elliptic curve cryptography? A. Efficiency of operation
B. Ease of implementation
C. symmetrical key exchange
D. resistance to quantum attacks. Answer: A QUESTION 373
A company has acquired a competitor whose network infrastructure uses only IPv6. An engineer must configure VPN access sourced from the new company. Which remote access VPN solution must be used? A. GET VPN
B. Any Connect
C. EzVPN
D. DMVPN Answer: C QUESTION 374
Which way to send OSPF routing updates over a site-to-site IPsec tunnel is true? A. Set the network type for the inside interface to nonbroadcast mode, and add the remote end as an OSPF neighbor.
B. Set the network type for the outside interface to broadcast mode, and add the headend device as an OSPF neighbor.
C. Set the network type for the DMZ interface to nonbroadcast mode, add the headend as an OSPF neighbor.
D. Set the network type for the outside interface to nonbroadcast mode, and add the remote end as an OSPF neighbor. Answer: D QUESTION 375
Which access lists are used in a typical IPsec VPN configuration? A. ACL to NAT traffic across the VPN tunnel
B. ACL to define policy based routing
C. ACL to define what traffic to exempt from NAT
D. ACL for routing neighbors across the tunnel Answer: C QUESTION 376
Which two parameters are specified in the isakmp (IKEv1) policy? (Choose two.) A. the peer
B. the hashing algorithm
C. the session key
D. the authentication method
E. the transform-set Answer: AD QUESTION 377
An engineer is assisting in the continued implementation of a VPN solution and discovers an NHRP server configuration. Which type of VPN solution has been implemented? A. DM VPN
B. IPsec VPN
C. SSL VPN
D. GET VPN Answer: A QUESTION 378
Which two options are purposes of the key server in Cisco IOS GETVPN? (Choose two.) A. to distributed static routing information
B. to authenticate group members
C. to define and distribute security policies
D. to distribute dynamic routing information
E. to encrypt transit data traffic. Answer: BE QUESTION 379
Refer to the Exhibit. Why is the tunnel not establishing?
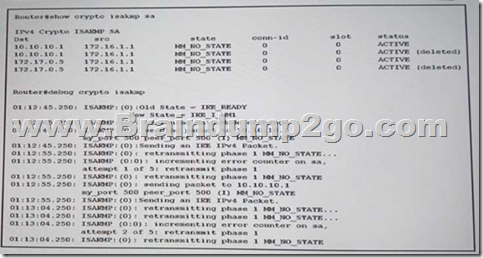 A. Lifetimes are misconfigured.
B. SAKMP packets are blocked.
C. NAT statements are missing.
D. GRE is not working correctly. Answer: B QUESTION 380
An engineer is configuring SSL VPN for remote access. A real-time application that is sensitive to packet delays will be used. Which feature should the engineer confirm is enabled to avoid latency and bandwidth problems associated with SSL connections? A. DTLS
B. DPD
C. SVC
D. IKEv2 Answer: A QUESTION 381
Which two operational advantages does Get VPN offer over site-to-site IPsec tunnel in a private MPLS-based core network? (Choose two.) A. Packets carry original source and destination IP addresses, which allows (or optimal routing of encrypted traffic.
B. Group Domain of Interpretation protocol allows for homomorphic encryption, which allows group members to operate on messages without decrypting them.
C. NETVPN is tunnel-less, which allows any group member to perform decryption and routing around network failures.
D. Key servers perform encryption and decryption of all the data in the network, which allows for tight security policies
E. Traffic uses one VRF to encrypt data and a different one to decrypt data, which allows for multicast traffic isolation Answer: AC
!!!RECOMMEND!!!1.|2018 Latest 300-209 Exam Dumps (PDF & VCE) 384Q&As Download: https://www.braindump2go.com/300-209.html
2.|2018 Latest 300-209 Study Guide Video: YouTube Video: YouTube.com/watch?v=IHRU47HQXac 1
|
