Microsoft 70-689 Certification New Released Sample Questions Free Download from Braindump2go (41-50)
Try 2015 Latet Updated 70-689 Practice Exam Questions and Answers, Pass 70-689 Actual Test 100% in 2015 New Year! Braindump2go Latest released Free Sample 70-689 Exam Questions are shared for instant download! Braindump2go holds the confidence of 70-689 exam candiates with Microsoft Official Guaranteed 70-689 Exa Dumps Products! 299 New Updated Questions and Answers! 2015 Microsoft 70-689 100% Success! Vendor: Microsoft
Exam Code: 70-689
Exam Name: Microsoft Upgrading Your Skills to MCSA Windows 8.1 
QUESTION 41
You update the video card driver on a computer that runs Windows 8.
You can no longer configure the display settings to extend the display to a projector.
You need to restore the display options as quickly as possible and retain all user data.
What should you do? A. Roll back the video card driver to the previous version.
B. Run the DisplaySwitch/extend command.
C. Run the sic /scannow command.
D. start the computer from the Windows 8 installation media and perform a system image
recovery. Answer: A QUESTION 42
A company has client computers that run Windows 8.
Each computer has two hard drives.
You need to create a dynamic volume on each computer that maximizes write performance. Which kind of dynamic volume should you create? A. Striped volume
B. RAID 5 volume
C. Spanned volume
D. Mirrored volume Answer: A QUESTION 43
A company has client computers that run Windows 8.
The corporate network is configured for tPv4 and IPv6.
You need to disable Media Sensing for IPv6 on the client computers without affecting IPv4 communications.
What should you do on each client computer? A. Run the Disable-NetAdapterBinding Windows PowerShell cmdlet.
B. Run the Disable-NetAdapter Windows PowerShell cmdlet.
C. Run the Set-NetlPv6Protocol Windows PowerShell cmdlet.
D. Run the Set-NetlPv4Protocol Windows PowerShell cmdlet. Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/hh826144.aspx 1
Set-NetIPv6Protocol [-DhcpMediaSense<DhcpMediaSense>]
Modifies the DHCPMediaSense property. This parameter value provides a mechanism for the network adapter to notify the protocol stack of media connect and disconnect events.
These events trigger the DHCP client to take some action, such as attempting to renew a DHCP lease or removing routes related to a disconnected network.
One application of Media Sense enables the network parameters on the notebook computer of a roaming user to automatically and transparently update without rebooting when the user moves from one location to another.
The acceptable values for this parameter are:
- Enabled: DhcpMediaSense set to Enabled.
- Disabled: DhcpMediaSense is set to Disabled.
The default value is Enabled. QUESTION 44
A company has 100 client computers that run Windows 8.
The client computers are members of a workgroup.
A custom application requires a Windows Firewall exception on each client computer.
You need to configure the exception on the client computers without affecting existing firewall settings.
Which Windows PowerShell cmdlet should you run on each client computer? A. New-NetFirewallRule
B. Set-NetFirewallSetting
C. Set-NetFirewallRule
D. Set-NetFirewallProfile
E. New-NetIPSecMainModeRule Answer: A
Explanation:
Creates a new inbound or outbound firewall rule and adds the rule to the target computer.
http://technet.microsoft.com/en-us/library/jj554908.aspx 2
DisplayName "Allow Inbound Telnet"-Direction Inbound-Program %SystemRoot% New-NetFirewallRule-System32tlntsvr.exe-RemoteAddress LocalSubnet-Action Allow QUESTION 45
A company has an Active Directory Domain Services (AD DS) domain.
All client computers run Windows 8 and are members of the domain.
Client computers maintain a list of sites in the Internet Explorer Restricted Sites security zone. Users of one client computer are able to download and install an application from a site within the Restricted Sites zone.
You need to ensure that users of the computer can install applications only from sites that are not in the Restricted Sites zone.
What should you do? A. Run the Set-ExecutionPolicy Windows PowerShell cmdlet.
B. Configure the Software Restriction Policy settings in the local Group Policy of the computer.
C. Add the blocked application as a software restriction policy to the GPO that configures
AppLocker.
D. Run the Cet-AppLockerPolicy Windows PowerShell cmdlet.
E. Add the blocked application as an additional AppLocker rule to the GPO that configures
AppLocker. Answer: B
Explanation:
Only Software Restriction policy allows for the control of applications from a network zone; AppLocker does not. 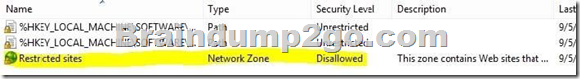
QUESTION 46
A company has an Active Directory Domain Services (AD DS) domain.
All client computers run Windows 8. A local printer is shared from a client computer.
The client computer user is a member of the Sales AD security group.
You need to ensure that members of the Sales security group can modify the order of documents in the print queue, but not delete the printer share.
Which permission should you grant to the Sales group?
A. Manage queue
B. Manage this printer
C. Print
D. Manage spooler
E. Manage documents Answer: E QUESTION 47
Your computer runs Windows 8 and is connected to an Active Directory Domain Services (AD DS) domain.
You create a folder and share the folder with everyone in your organization.
You need to modify the NTFS permissions of the folder to meet the following criteria:
- Users from the Marketing security group must be able to open files, but not modify them.
- Users from the Supervisors security group must be able to create, modify, and delete files.
Which permissions should you set? Users from both groups must not be able to delete the folder. A. Assign the Marketing group the Read permission.
Assign the Supervisors group the Read and Write permissions and the Delete Subfolders
and Files special permission.
B. Assign the Marketing group the Read and Write permissions.
Assign the Supervisors group the Full Control permission.
C. Assign the Marketing group the Read and Write permissions.
Assign the Supervisors group the Modify permission and the Delete Subfolders and Files
special permission.
D. Assign the Marketing group the Read permission.
Assign the Supervisors group the Read and Write permissions and the Delete special
permission. Answer: A QUESTION 48
A company has client computers that run Windows 8.
The company implements the following security requirements:
- All client computers must use two-factor authentication.
- At least one authentication method must include exactly four characters or gestures.
You need to choose authentication methods that comply with the security requirements.
Which two authentication methods should you choose? (Each correct answer presents part of the solution. Choose two.) A. PIN
B. Biometric authentication
C. Picture password
D. Microsoft account Answer: AB
Explanation:
Something the user knows: PIN (4 digits)
One might be tempted to think the photo for the picture password is something the User has.
But it is something the User knows, too:
He knows how to draw the gestures (maximum 3 gestures supported with picture password),
and it is no physical object (like a token, smart card ...)
The MS Account is too something the user knows.
So the answer must be Biometric authentication.
Two-factor authentication requires the use of two of the three authentication factors:
Something the user knows (e.g., password, PIN);
Something the user has (physical Object) (e.g., ATM card, smart card);
and Something the user is (e.g., biometric characteristic, such as a fingerprint).
The factors are identified in the standards and regulations for access to U.S. Federal Government systems. QUESTION 49
A company has client computers that run Windows 8.
The company implements the following security requirements:
- All client computers must use two-factor authentication.
- At least one authentication method must include more than four characters or gestures.
You need to choose authentication methods that comply with the security requirements.
Which two authentication methods should you choose? (Each correct answer presents part of the solution. Choose two.) A. PIN
B. Biometric authentication
C. Picture Password
D. Microsoft Account Answer: BD
Explanation:
More than 4 characters are of course supported with the Microsoft Account.
It is something the user knows. The picture password would be another thing the user knows (gestures). So there's only MS Account and Biometric authentication left.
Two-factor authentication requires the use of two of the three authentication factors:
Something the user knows (e.g., password, PIN);
Something the user has (physical Object) (e.g., ATM card, smart card);
and Something the user is (e.g., biometric characteristic, such as a fingerprint).
The factors are identified in the standards and regulations for access to U.S. Federal Government systems. QUESTION 50
Your computer runs Windows 8 and is connected to an Active Directory Domain Services (AD DS) domain.
You create a folder and share the folder with everyone in your organization.
You need to modify the NTFS permissions of the folder to meet the following criteria:
- Users from the Supervisors AD security group must be able to open files, but not modify them.
- Users from the Marketing AD security group must be able to create, modify, and delete files.
- Users from both groups must not be able to delete the folder.
Which permissions should you set? A. Assign the Supervisors group the Read and Write permissions.
Assign the Marketing group the Modify permission and the Delete Subfolders and Files
special permission.
B. Assign the Supervisors group the Read and Write permissions.
Assign the Marketing group the Full Control permission.
C. Assign the supervisors group the Read permission.
Assign the Marketing group the Read and Write permissions and the Delete Subfolders
and Files special permission.
D. Assign the Supervisors group the Read permission.
Assign the Marketing group the Read and Write permissions and the Delete special
permission. Answer: C
2015 Latest Released Microsoft 70-689 Exam Dumps Free Download From Braindump2go Now! All Questions and Answers are chcked again by Braindump2go Experts Team, 100% Real Questions and Correct Answers Guaranteed! Full Money Back Guarantee Show our Confidence in helping you have a 100% Success of Exam 70-689! Just have a try! 
http://www.braindump2go.com/70-689.html
|


