MICROSOFT OFFICIAL: New Updated 70-410 Exam Questions from Braindump2go 70-410 pdf dumps and 70-410 vce dumps! Welcome to download the newest Braindump2go 70-410 vce&pdf dumps: http://www.braindump2go.com/70-410.html (471 Q&As)
All Latest Updated Questions and Answers in Braindump2go 70-410 Exam Dumps will not take you a lot of time to comprehend and you can easily cover up the entire Microsoft 70-410 syllabus for your examination.Download Braindump2go Free 70-410 Sample Questions Now, Pass 70-410 Exam in advance!
Exam Code: 70-410
Exam Name Installing and Configuring Windows Server 2012
Certification Provider: Microsoft
Corresponding Certifications: MCSA, MCSA: Windows Server 2012, MCSE, MCSE: Desktop Infrastructure, MCSE: Private Cloud, MCSE: Server Infrastructure
Keywords:70-410 Dumps,70-410 Exam Questions,70-410 VCE,70-410 VCE Free,70-410 PDF,70-410 Lab Manual PDF,70-410 Practice Exams,70-410 Practice Tests,70-410 Installing and Configuring Windows Server 2012
QUESTION 71
Your company has a main office and two branch offices. The offices connect to each other by using a WAN link. In the main office, you have a server named Server1 that runs Windows Server 2012 R2. Server1 is configured to use an IPv4 address only.
You need to assign an IPv6 address to Server1. The IP address must be private and routable. Which IPv6 address should you assign to Server1?
A. fe80:ab32:145c::32cc:401b
B. ff00:3fff:65df:145c:dca8::82a4
C. 2001:ab32:145c::32cc:401b
D. fd00:ab32:14:ad88:ac:58:abc2:4
Answer: D
Explanation:
pg 266 Chapter 6 : Installing and Configuring Windows Server 2012 R2 Unique local addresses
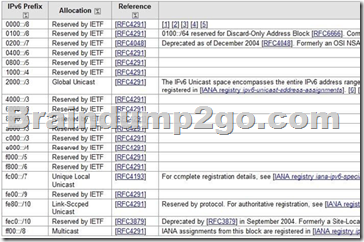
Unique local addresses are IPv6 addresses that are private to an organization in the same way that private addresses–such as 10.x.x.x, 192.168.x.x, or 172.16.0.0 172.31.255.255–can be used on an IPv4 network.
Unique local addresses, therefore, are not routable on the IPv6 Internet in the same way that an address like 10.20.100.55 is not routable on the IPv4 Internet. A unique local address is always structured as follows:
The first 8 bits are always 11111101 in binary format. This means that a unique local address always begins with FD and has a prefix identifier of FD00::/8.
QUESTION 72
Your network contains an Active Directory domain named contoso.com. All client computers run Windows 8.
You deploy a server named Server1 that runs Windows Server 2012 R2.
You install a new client-server application named App1 on Server1 and on the client computers. The client computers must use TCP port 6444 to connect to App1 on Server1. Server1 publishes the information of App1 to an intranet server named Server2 by using TCP port 3080.
You need to ensure that all of the client computers can connect to App1.
The solution must ensure that the application can connect to Server2.
Which Windows Firewall rule should you create on Server1?
A. an inbound rule to allow a connection to TCP port 3080
B. an outbound rule to allow a connection to TCP port 3080
C. an outbound rule to allow a connection to TCP port 6444
D. an inbound rule to allow a connection to TCP port 6444
Answer: D
Explanation:
A. Server2 needs inbound on 3080
B. All ports outbound allowed by default
D. Server1 gets request from Client PC’s it needs a inbound rule for 6444
By default, Windows Firewall with Advanced Security blocks all unsolicited inbound networktraffic, and allows all outbound network traffic. For unsolicited inbound network traffic to reach your computer, you must create an allow rule to permit that type of network traffic. If a network program cannot get access, verify that in the Windows Firewall with Advanced Security snap-in there is an active allow rule for the current profile. To verify that there is an active allow rule, double-click Monitoring and then click Firewall.
If there is no active allow rule for the program, go to the Inbound Rules node and create a new rule for that program. Create either a program rule, or a service rule, or search for a group that applies to the feature and make sure all the rules in the group are enabled. To permit the traffic, you must create a rule for the program that needs to listen for that traffic. If you know the TCP or UDP port numbers required by the program, you can additionally restrict the rule to only those ports, reducing the vulnerability of opening up all ports for the program.
http://social.technet.microsoft.com/wiki/contents/articles/13894.troubleshooting-windows-firewall-with-advanced-security-in-windows-server-2012.aspx
QUESTION 73
Your network contains an Active Directory domain named contoso.com.
All user accounts in the sales department reside in an organizational unit (OU) named OU1.
You have a Group Policy object (GPO) named GPO1. GPO1 is used to deploy a logon script to all of the users in the sales department.
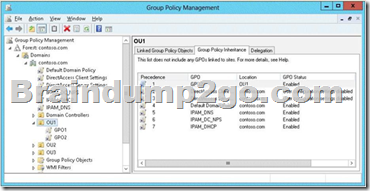
You discover that the logon script does not run when the sales users log on to their computers. You open Group Policy Management as shown in the exhibit.
You need to ensure that the logon script in GPO1 is applied to the sales users.
What should you do?
A. Enforce GPO1.
B. Modify the link order of GPO1.
C. Modify the Delegation settings of GPO1.
D. Enable the link of GPO1.
Answer: D
Explanation:
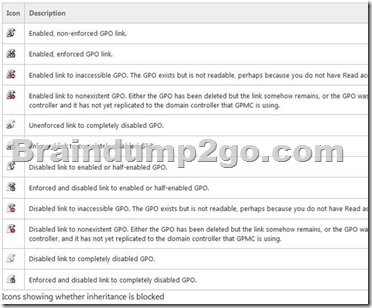
D. GPO1 needs to be linked to OU1
http://technet.microsoft.com/en-us/library/cc732979.aspx
http://technet.microsoft.com/en-us/library/cc776004%28v=ws.10%29.aspx#BKMK_icons_link
QUESTION 74
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2012 R2.
The domain contains a server named Server1.
You install the Windows PowerShell Web Access gateway on Server1.
You need to provide administrators with the ability to manage the servers in the domain by using the Windows PowerShell Web Access gateway.
Which two cmdlets should you run on Server1? (Each correct answer presents part of the solution. Choose two.)
A. Set-WSManQuickConfig
B. Set-WSManInstance
C. Add-PswaAuthorizationRule
D. Set-BCAuthentication
E. Install-PswaWebApplication
Answer: CE
Explanation:
A. Configures the local computer for remote management.
B. Modifies the management information that is related to a resource.
C. Adds a new authorization rule to the Windows PowerShell Web Access authorization rule set. D. Specifies the BranchCache computer authentication mode.
E. Configures the Windows PowerShell ® Web Access web Application in IIS.
http://technet.microsoft.com/en-us/library/hh849867.aspx
http://technet.microsoft.com/en-us/library/hh849875.aspx
http://technet.microsoft.com/en-us/library/jj592890(v=wps.620).aspx http://technet.microsoft.com/en-us/library/hh848404(v=wps.620).aspx http://technet.microsoft.com/en-us/library/jj592894(v=wps.620).aspx
QUESTION 75
You have a server named Server 1 that runs Windows Server 2012 R2. Server 1 has the Hyper-V server role installed.
You have fixed-size VHD named Files.vhd.
You need to make the contents in Files.vhd available to several virtual machines. The solution must meet the following requirements:
– Ensure that if the contents are changed on any virtual machine, the changes are not reflected on the other virtual machines.
– Minimize the amount of disk space used.
What should you do?
A. Create a fixed-size VHDX. Transfer the information from Files.vhd to the new VHDX file.
B. Convert Files.vhd to a dynamically expanding VHD?
C. Create a dynamically expanding VHDX. Transfer the information from Files.vhd to the new VHDX file.
D. Create differencing VHDs that use Files.vhd as the parent disk.
Answer: D
Explanation:
A. A conversion would be needed from VHD to VHDX. Not available to multiple VM’s
B. Single VHD not available to multiple VM’s. Changes wouldn’t be reflected
C. A conversion would be needed from VHD to VHDX. Not available to multiple VM’s
D. Child disk for multiple VM’s with Files.vhd as parent A differencing disk is associated with another virtual hard disk that you select when you create the differencing disk. This means that the disk to which you want to associate the differencing disk must exist first. This virtual hard disk is called the “parent” disk and the differencing disk is the “child” disk.
The parent disk can be any type of virtual hard disk.
The differencing disk stores all changes that would otherwise be made to the parent disk if the differencing disk was not being used. The differencing disk provides an ongoing way to save changes without altering the parent disk.
You can use the differencing disk to store changes indefinitely, as long as there is enough space on the physical disk where the differencing disk is stored. The differencing disk expands dynamically as data is written to it and can grow as large as the maximum size allocated for the parent disk when the parent disk was created.
http://technet.microsoft.com/en-us/library/cc720381(v=ws.10).aspx
QUESTION 76
Your network contains an Active Directory domain named adatum.com. The domain contains several thousand member servers that run Windows Server 2012 R2. All of the computer accounts for the member servers are in an organizational unit (OU) named ServersAccounts. Servers are restarted only occasionally.
You need to identify which servers were restarted during the last two days.
What should you do?
A. Run dsquery computer and specify the -stalepwd parameter
B. Run dsquery server and specify the -o parameter.
C. Run Get-ADComputer and specify the lastlogon property.
D. Run Get-ADComputer and specify the SearchScope parameter
Answer: C
Explanation:
A. dsquery computer -stalepwdnumber_of_days – Searches for all computers that have not changed theirpassword for the specified number_of_days.
B. dsquery server -o {dn | rdn | samid} – Specifies the format in which the list of entries found by the search willbe displayed: dn distinguished name of each entry, default; rdn relative distinguished name of each entry;
samid SAM account name of each entry computer group server user; upn user principal name of each entryuser
C. Gets one or more Active Directory computers lastLogondate should be used
D. SearchScope specifies the scope of an Active Directory search. Possible values for this parameter are:
Base or 0; OneLevel or 1; Subtree or 2 – A Base query searches only the current path or object.
A One Level query searches the immediate children of that path or object.
A Subtree query searches the current path orobject and all children of that path or object.
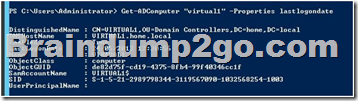
http://technet.microsoft.com/en-us/library/ee617192.aspx
http://technet.microsoft.com/en-us/library/cc732952(v=ws.10).aspx
QUESTION 77
Your network contains three servers that run Windows Server 2012 R2. The servers are configured as shown in the following table (click Exhibit). Server3 is configured to obtain an IP address automatically.
You need to ensure that Server3 only receives an IP address from Server1.
The IP address must always be the same.
Which two tasks should you perform? (Each correct answer presents part of the solution. Choose two.)
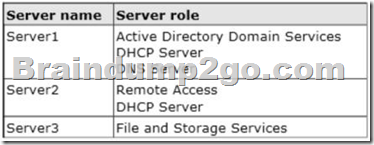
A. Create an exclusion on Server1.
B. Create a filter on Server1.
C. Create a reservation on Server2
D. Create a reservation on Server1
E. Create a filter on Server2.
Answer: DE
Explanation:
A. Exclude range of IP’s for lease
B. Wrong Server
C. Wrong Sever
D. For clients that require a constant IP address, you can either manually configure a static IP address,or assign a reservation on the DHCP server
E. DHCP Deny Filter at Server2 to exclude MAC address of Server3 MAC address filterEnable and define an explicit allow list. The DHCP server provides DHCP services only to clients whose MACaddresses are in the allow list. Any client that previously received IP addresses is denied address renewal if its MAC address isn’t onthe allow list.
Enable and define an explicit deny list. The DHCP server denies DHCP services only to clients whose MACaddresses are in the deny list.
Any client that previously received IP addresses is denied address renewal if its MAC address is on thedeny list.
Enable and define an allow list and a block list.
The block list has precedence over the allow list. This means that the DHCP server provides DHCPservices only to clients whose MAC addresses are in the allow list, provided that no corresponding matchesare in the deny list.
If a MAC address has been denied, the address is always blocked even if the address is on the allowlist.
http://technet.microsoft.com/en-us/library/cc754537(v=ws.10).aspx http://technet.microsoft.com/en-us/magazine/ff521761.aspx
http://technet.microsoft.com/en-us/library/cc779507(v=ws.10).aspx
QUESTION 78
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2 and a client computer named Computer1 that runs Windows 8. DC1 is configured as a DHCP server as shown in the exhibit. (Click the Exhibit button.) Computer1 is configured to obtain an IP address automatically.
You need to ensure that Computer1 can receive an IP address from DC1.
What should you do?
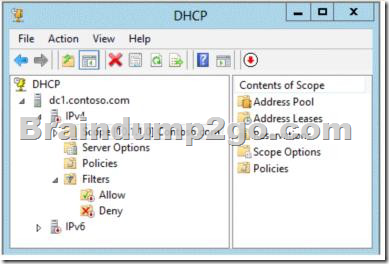
A. Disable the Allow filters.
B. Disable the Deny filters
C. Activate Scope [10.1.1.0] Contoso.com.
D. Authorize dc1.contoso.com.
Answer: D
Explanation:
Red down arrow indicates a unauthorized DHCP server A DHCP server that is a domain controller or a member of an Active Directory domain queries Active Directoryfor the list of authorized servers (identified by IP address). If its own IP address is not in the list of authorized DHCP servers, the DHCP Server service does not completeits startup sequence and automatically shuts down. http://technet.microsoft.com/en-us/library/cc754792.aspx
http://technet.microsoft.com/en-us/library/ee941131(v=ws.10).aspx http://technet.microsoft.com/en-us/library/gg722802(v=ws.10).aspx
http://pc-addicts.com/server-2012-dhcp-server-role/
QUESTION 79
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named Server1 that has the DNS Server server role installed. Server1 hosts a primary zone for contoso.com. The domain contains a member server named Server2 that is configured to use Server1 as its primary DNS server. From Server2, you run nslookup.exe as shown in the exhibit. (Click the Exhibit button.)
You need to ensure that when you run Nslookup, the correct name of the default server is displayed.
What should you do?
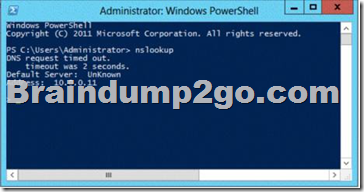
A. From Advanced TCP/IP Settings on Server1, add contoso.com to the DNS suffix list
B. On Server1, modify the Security settings of the contoso.com zone
C. On Server1, create a reverse lookup zone.
D. From Advanced TCP/IP Settings on Server2, add contoso.com to the DNS suffix list
Answer: C
Explanation:
C. Make sure that a reverse lookup zone that is authoritative for the PTR resource record exists. For more information about adding a reverse lookup zone, see “Adding a Reverse Lookup Zone” http://technet.microsoft.com/en-us/library/cc961417.aspx
QUESTION 80
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that hosts the primary DNS zone for contoso.com. All client computers are configured to use DC1 as the primary DNS server.
You need to configure DC1 to resolve any DNS requests that are not for the contoso.com zone by querying the DNS server of your Internet Service Provider (ISP).
What should you configure?
A. Name server (NS) records
B. Condition& forwarders
C. Forwarders
D. Naming Authority Pointer (NAPTR) DNS resource records (RR)
Answer: C
Explanation:
A. Specifies a name server for the domain, which allows DNS lookups within various zones. Each primary andsecondary name server should be declared through this record.
B. http://windowsitpro.com/networking/q-whats-conditional-dns-forwarding
C. manage the Domain Name System (DNS) traffic between your network and the Internet
D.Configure forwarders to send DNS queries directly to your ISP’s DNS server or other DNS servers. Most of the time, when you configure forwarders, DNS performance and efficiency increases, but thisconfiguration can also introduce a point of failure if the forwarding DNS server is experiencing problems.
A forwarder is a Domain Name System (DNS) server on a network used to forward DNS queries for externalDNS names to DNS servers outside of that network. A DNS server on a network is designated as a forwarder by having the other DNS servers in the networkforward the queries they cannot resolve locally to that DNS server. By using a forwarder, you can manage name resolution for names outside of your network, such as names onthe Internet, and improve the efficiency of name resolution for the computers in your network.
http://social.technet.microsoft.com/Forums/en-US/winserverNIS/thread/2f35cae2-341c4bfe-9dac- 724ddace6d51/
http://technet.microsoft.com/en-us/library/cc722542.aspx
http://technet.microsoft.com/en-us/library/cc754931.aspx
Braindump2go New Published Exam Dumps: Microsoft 70-410 Practice Tests Questions, 471 Latest Questions and Answers from Official Exam Centre Guarantee You a 100% Pass! Free Download Instantly!
70-410 PDF Dumps & 70-410 VCE Dumps Full Version Download(471q): http://www.braindump2go.com/70-410.html