May/2020 New Braindump2go 200-901 PDF and 200-901 VCE Dumps Free Updated Today! Following are some new 200-901 Exam Questions.
QUESTION 75
You are developing a YANG-based policy model to encode the type of entity that is connected to a given interface, such as partner, supplier, customer, or distributor. Which YANG statement limits any configuration action?
A. when
B. case
C. enumeration
D. contains
Correct Answer: A
QUESTION 76
Which two network configuration protocols use XML as a data representation format? (Choose two.)
A. NETCONF
B. CORBA
C. TOSGA
D. SNMP
E. RESTCONF
Correct Answer: AE
QUESTION 77
What are two advantages of version control software? (Choose two.)
A. It supports tracking and comparison of changes in binary formate files.
B. It allows old versions of packaged applications to be hosted on the Internet
C. It provides wiki collaboration software for documentation.
D. It supports comparisons between revisions of source code files.
E. It allows new team members to access the current code and history.
Correct Answer: AD
QUESTION 78
Which description of a default gateway if true?
A. It is a device that receives IP packets that have no explicit next-hop in the routing table.
B. It is a feature that translates between public and private addresses.
C. It is a security feature that denies certain traffic.
D. It is a device that receives Layer 2 frames with an unknown destination address.
Correct Answer: A
QUESTION 79
Which two descriptions can be given to an application that is interacting with a webhook? (Choose two.)
A. Processor
B. Codec
C. Listener
D. Receiver
E. Transaction monitor
Correct Answer: DE
QUESTION 80
Which action resolves a 401 error in response to an HTTP GET that is issued to retrieve a configuration statement using RESTCONF on a CSR 1000V?
A. Change the HTTP method to PUT.
B. Change the transport protocol to HTTPS.
C. Check the MIMF types in the HTTP headers.
D. Check the authentication credentials.
Correct Answer: B
QUESTION 84
Which communication mechanism does NETCONF use?
A. SOAP over HTTPS
B. YAML over SSH
C. YAML over HTTPS
D. RPC over SSH
Correct Answer: D
QUESTION 85
Management protocols like NETCONF access network elements on well-known ports. Which design practice hardens a network device implementation?
A. Specify the source interface for SSH .
B. Limit access to port 830, well-known clients, and SSH VTY.
C. Enable CoPP.
D. Configure ip http secure-server.
Correct Answer: B
QUESTION 86
Which action does the Git command git merge allow the development to perform?
A. Combine multiple sequences of commits into one unified history
B. Push changes to the remote repository
C. Switch between branches
D. Create, list, rename, and delete branches
Correct Answer: A
QUESTION 87
Refer to the exhibit. A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called “vegetables”. Using Python, which output is the result of this command?

print(filter(lambda 1: 1[ ‘type’ ] == ‘fruit’, vegetables) [0][‘items’][0][‘items’][0])
A. Lettuce
B. Kiwi
C. [`kiwi’, `grape’]
D. {‘color’: ‘green’, ‘items’: [‘kiwi’, ‘grape’]}
Correct Answer: B
QUESTION 88
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
A. 400
B. 403
C. 405
D. 429
Correct Answer: A
QUESTION 89
Refer to the exhibit. What is the function of the python script?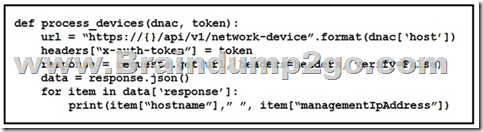
A. Count and print the total number of available devices.
B. Iterate over a list of network devices and write all device names and management IP addresses to an output file.
C. Iterate over a list of network devices and write all device type and associated management IP address.
D. For each device that is returned, display the device and, for each device, print the device name and management IP address.
E. Loop through the returned list of network devices and, for each device, print the device name management IP address.
Correct Answer: A
QUESTION 90
Which device is a system that monitors and controls incoming and outgoing network traffic based on predetermined security rules?
A. Switch
B. Router
C. Firewall
D. Load balancer
Correct Answer: C
QUESTION 91
What are two security benefits of a Docker-based application?
A. easier to patch because Docker containers include only dependencies that the application requires
B. prevents information leakage that can occur when unhandled exceptions are returned in HTTP responses
C. allows for separation of application that traditionally run in the same host
D. natively secures access to secrets that are used by the running application
E. guarantees container images are secured and free of vulnerabilities
Correct Answer: DE
Resources From:
1.2020 Latest Braindump2go 200-901 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/200-901.html
2.2020 Latest Braindump2go 200-901 PDF and 200-901 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1ypgUTJWhai6LLGstB79-TlJUmdC3sp0V?usp=sharing
3.2020 Free Braindump2go 200-901 PDF Download:
https://www.braindump2go.com/free-online-pdf/200-901-Dumps.pdf
https://www.braindump2go.com/free-online-pdf/200-901-PDF.pdf
https://www.braindump2go.com/free-online-pdf/200-901-PDF-Dumps.pdf
https://www.braindump2go.com/free-online-pdf/200-901-VCE.pdf
https://www.braindump2go.com/free-online-pdf/200-901-VCE-Dumps.pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!