(Jun-2016-Updated)Microsoft 70-243 VCE Dumps Free Shared - Braindump2go(NQ81-NQ90)
2016 June Microsoft Official: 70-243 PDF & 70-243 VCE Dumps with 154Q New 70-243 Exam Questions New Updated By Braindump2go.com Today! Free Dowbload 70-243 Exam Dumps Today! 100% Exam Pass Guaranteed!
NEW QUESTION 81 - NEW QUESTION 90 QUESTION 81
Your network contains a System Center 2012 Configuration Manager environment.
The hierarchy contains a Central Administration site named Site1 and a primary site named
Site2.
You discover that none of the packages created on Site1 are displayed in Site2.
You need to identify whether there is a replication issue between the sites.
What should you review? A. The Microsoft SQL Server transaction log files
B. The Colleval.log file
C. The Replmgr.log file
D. The Dataldr.log file Answer: C
Explanation:
Replmgr.log
Records the replication of files between the site server components and the Scheduler
component.
Update:
It seems that more recent exams contain the answer "the Rcmctrl.log file"
So if you are lucky and have it, choose this one. QUESTION 82
Your network contains a Windows Server Update Services (WSUS) server.
All client computers are configured as WSUS clients. All of the client computers have Windows Firewall enabled. Windows Firewall is configured to allow Fie and Printer Sharing.
Users are not configured as local Administrators on their client computers.
You deploy System Center 2012 Configuration Manager.
You need to identify which methods you can use to deploy the Configuration Manager client to an of the client computers.
Which client installation methods should you identify? (Choose all that Apply.) A. a logon script installation
B. a manual client installation
C. a software update-based client installation
D. a Client Push Installation
E. an Active Directory Group Policy-based installation Answer: CDE
Explanation:
The Logon script runs with the user's credentials.
Manual installation also runs with the user's credentials.
Software update point uses the Local System account and All client computers are configured as WSUS clients. So the firewall should not affect functionality.
Client Push Installation requires File and Printer Sharing.
Group Policy Installation requires File and Printer Sharing.
http://technet.microsoft.com/en-us/library/gg682191.aspx 1 QUESTION 83
Your company uses System Center 2012 R2 Configuration Manager Service Pack 1 (SP1) to distribute operating system images. The standard operating system for client computers is Windows 8.1 Enterprise (x86).
You receive 300 new desktop computers. Each computer has a new storage controller.
When you attempt to deploy an existing image to one of the computers, you receive an error message indicating that a storage device cannot be found during the pre-boot deployment phase.
You need to ensure that you can deploy Windows 8.1 to the new computers by using an image.
What should you do? A. Import the storage drivers to the Drivers container and update the task sequence.
B. Create a new x64 boot image and configure the operating system image to use the x64 boot image.
C. Create a new driver package and update the task sequence.
D. Update the existing x86 boot image to include the storage drivers. Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/gg712674.aspx 2
Planning a Device Driver Strategy in Configuration Manager
You can add Windows device drivers that have been imported into the driver catalog to boot images. Use the following guidelines when you add device drivers to a boot image:
* Add only mass storage and network adapter device drivers to boot images because other types of drivers are not generally required. Drivers that are not required increase the size of the boot image unnecessarily.
* Add only device drivers for Windows 7 to a boot image because the required version of Windows PE is based on Windows 7.
* Ensure that you use the correct device driver for the architecture of the boot image. Do not add an x86 device driver to an x64 boot image. QUESTION 84
Your network contains a System Center 2012 Configuration Manager environment.
You plan to create a build and capture a task sequence to build a reference image of Windows 7. You need to identify which Application must exist in Configuration Manager before you can create the build and capture the task sequence.
Which Applications should you identify? (Choose all that Apply.) A. Microsoft Deployment Toolkit (MDT)
B. Configuration Manager client
C. System Preparation tool (Sysprep)
D. User State Migration Tool (USMT) Answer: AC
Explanation:
http://technet.microsoft.com/en-us/library/bb633062.aspx 3
How to Create a Task Sequence to Build and Capture an Operating System Image
You can create task sequence to build and capture operating system image for use with operating system deployment using the New Task Sequence Wizard. After you have created the task sequence, you can edit the task sequence by selecting the Task Sequences node and right-clicking on the task sequence you want to change and selecting Edit to launch the Task Sequence Editor. QUESTION 85
You are the network administrator for a company named Contoso, Ltd. The network contains 1,000 desktop computers and 500 servers. The network contains a System Center 2012 Configuration Manager environment. The names of all the desktop computers in the human resources department start with the letters HR, for example HR001 and HR023. A device collection named All Server Devices contains all of the servers.
A device collection named All Desktop Devices contains all of the desktop computers.
You plan to create a new collection named All HR Computers and Servers. The new collection must contain all of the human resources department computers and all of the servers.
The collection must not contain any other computers.
You need to create a membership rule for the new collection.
Which rule should you include in the membership rule? (Choose all that Apply.) A. QUERY RULE: select * from SMS_R_System where SMS_R_system.NetbiosName like "HR%"
B. INCLUDE RULE: All Server Devices
C. EXCLUDE RULE: All NON HR Computers
D. EXCLUDE RULE: All Desktop Devices
E. QUERY RULE- select * from SMS_R_System where
SMS_R_system.OperatingSystemNameandVersion like. *%Workstation*
F. QUERY RULE- select * from SMS_R_System where
SMS_R_system.OperatingSystemNameandVersion not like. *%Server* Answer: AB
Explanation:
select * from SMS_R_System where SMS_R_system.NetbiosName like "HR%"
SQL command to select all Systems whose names begin with HR
INCLUDE RULE: All Server Devices
Selects all the Server Devices as asked in the question.
Further information:
http://technet.microsoft.com/en-us/library/gg682177.aspx 4
Introduction to Collections in Configuration Manager
Collections in System Center 2012 Configuration Manager represent logical groupings of resources, such as users and devices.
You can use collections to help you perform many tasks, such as managing applications, deploying compliance settings, or installing software updates. You can also use collections to manage groups of client settings.
Additionally, System Center 2012 Configuration Manager uses collections with role-based administration to specify the collections that an administrative user can access.
Collection Rules
Direct Rule
Query Rule
Query rules dynamically update the membership of a collection based on a query that Configuration Manager runs on a schedule.
Unlike direct rule collections, this collection membership automatically updates when you add or remove new users to the Human Resources organizational unit.
Include Collections Rule
The include collections rule lets you include the members of another collection in a Configuration Manager collection. Configuration Manager updates the membership of the current collection on a schedule if the membership of the included collection changes.
Exclude Collections Rule
The exclude collections rule lets you exclude the members of another collection from a Configuration Manager collection. Configuration Manager updates the membership of the current collection on a schedule if the membership of the excluded collection changes.
Note: If a collection includes both include collection and exclude collection rules and there is a conflict, the exclude rule takes priority over the include rule.
Default Collections in Configuration Manager
All User Groups
All Users
All Users and User Groups
All Mobile Devices
All Systems
All Unknown Computers QUESTION 86
Drag and Drop Question
Your network contains a System Center 2012 Configuration Manager environment.
Three users named User1, User2, and User3 will perform the following tasks:
- User1 will review software metering data and inventory reports.
- User2 will deploy Applications and create alerts.
- User3 will create configuration items.
You need to identify which security role must be assigned to which user.
What should you identify?
To answer, drag the appropriate security role to the correct user in the answer area. Each security role may be used once, more than once, at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
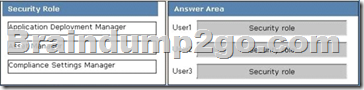
Answer:
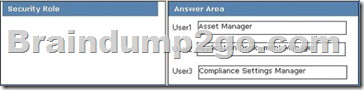
Explanation:
Asset Manager
Grants permissions to manage the Asset Intelligence Synchronisation Point, Asset Intelligence reporting classes, software inventory, and metering rules Application Deployment Manager Grants permissions to deploy applications. Administrative users who are associated with this role can view a list of applications, and they can manage deployments for applications, alerts, templates, and packages, and programs. Administrative users who are associated with this role can also view collections and their members, status messages, queries, and conditional delivery rules.
Compliance Settings Manager
Grants permissions to define and monitor Compliance Settings. Administrative users associated with this role can create, modify and delete configuration items and baselines to collections, and initiate compliance evaluation, and initiate remediation for non-compliant computers. QUESTION 87
Your network contains a System Center 2012 Configuration Manager environment.
The Client Status node .n the Configuration Manager console shows a downward trend in client health.
You verify the logs on several clients.
You discover that the clients are healthy and are communicating normally to management points. You need to identify the reasons why the Configuration Manager console displays a downward trend in client health.
Which reasons should you identify? (Choose all that Apply.) A. In Client Status Settings Properties, the Heartbeat discovery during the following days interval is
shorter than the Heartbeat Discovery interval.
B. The age set in the Delete Aged Discovery Data maintenance task is shorter than the Heartbeat
Discovery interval.
C. The Delete Obsolete Client Discovery Data maintenance task is disabled.
D. The Active Directory sites that are members of boundary groups are modified.
E. Microsoft SQL Server replication to the management points stopped. Answer: BD
Explanation:
http://technet.microsoft.com/en-us/library/gg712308.aspx#BKMK_HeartbeatDisc 5
Planning for Discovery in Configuration Manager - About Heartbeat Discovery
Heartbeat Discovery differs from other Configuration Manager discovery methods. It is enabled by default and runs on each computer client to create a discovery data record (DDR).
Heartbeat Discovery runs either on a schedule configured for all clients in the hierarchy, or if manually invoked, on a specific client by running the Discovery Data Collection Cycle on the Action tab in a client's Configuration Manager program. When Heartbeat Discovery runs, it creates a discovery data record (DDR) that contains the client's current information including network location, NetBIOS name, and operational status details. It is a small file, about 1KB, which is copied to a management point, and then processed by a primary site. The submission of a Heartbeat Discovery DDR can maintain an active client's record in the database, and also force discovery of an active client that might have been removed from the database, or that has been manually installed and not discovered by another discovery method.
The default schedule for Heartbeat Discovery is set to every 7 days. If you change the heartbeat discovery interval, ensure that it runs more frequently than the site maintenance task Delete Aged Discovery Data, which deletes inactive client records from the site database. You can configure the Delete Aged Discovery Data task only for primary sites.
http://technet.microsoft.com/en-us/library/gg712679.aspx 6
Planning for Boundaries and Boundary Groups in Configuration Manager
In System Center 2012 Configuration Manager, a boundary is a network location on the intranet that can contain one or more devices that you want to manage. Boundaries can be an IP subnet, Active Directory site name, IPv6 Prefix, or an IP address range, and the hierarchy can include any combination of these boundary types. To use a boundary, you must add the boundary to one or more boundary groups. Boundary groups are collections of boundaries. By using boundary groups, clients on the intranet can find an assigned site and locate content when they have to install software, such as applications, software updates, and operating system images.
When clients are on the Internet, or they are configured as Internet-only clients, they do not use boundary information. These clients cannot use automatic site assignment and always download content from any distribution point in their assigned site when the distribution point is configured to allow client connections from the Internet.
Site Assignment
You can configure each boundary group with an assigned site for clients. Clients join the assigned site of a boundary group that contains the client's current network location. When a boundary is added to multiple boundary groups that have different assigned sites, clients will nondeterministically select one of the sites. System Center 2012 Configuration Manager does not support this overlapping boundary configuration for site assignment.
If you make a change to the site assignment configuration of a boundary group, only new site assignment actions are affected. Clients that have previously been assigned to a site, do not re-evaluate their site assignment based on changes to the configuration of a boundary group.
Further information:
http://technet.microsoft.com/en-us/library/bb632879.aspx 7
Delete Obsolete Client Discovery Data Task Overview
The Delete Obsolete Client Discovery Data task deletes obsolete client records from the Configuration Manager 2007 site database. A record that is marked obsolete typically was superseded by a newer record for the same client. The newer record becomes the client's current record, and the older record becomes obsolete.
When you enable this task, you should configure the schedule to run at an interval greater than the heartbeat discovery schedule. This allows clients to send Discovery Data Records (DDRs) so that the obsolete bit is set correctly.
http://technet.microsoft.com/en-us/library/gg682132.aspx#BKMK_ClientHealth 8
Introduction to Client Deployment in Configuration Manager - Monitoring the Status of Client Computers in Configuration Manager
Use the Client Status node in the Monitoring workspace of the Configuration Manager console to monitor the health and activity of client computers in your hierarchy.
Configuration Manager uses the following two methods to evaluate the overall status of client computers.
Client Activity: You can configure thresholds to determine whether a client is active, for example:
Whether the client requested policy during the last seven days.
Whether Heartbeat Discovery found the client during the last seven days.
Whether the client sent hardware inventory during the last seven days.
When all these thresholds are exceeded, the client is determined to be inactive.
Client Check: A client evaluation engine is installed with the Configuration Manager client, which periodically evaluates the health of the Configuration Manager client and its dependencies. This engine can check or remediate some problems with the Configuration Manager client.
Client status uses the monitoring and reporting capabilities of Configuration Manager to provide information in the Configuration Manager console about the health and activity of the client.
You can configure alerts to notify you when clients check results or client activity drops below a specified percentage of clients in a collection or when remediation fails on a specified percentage of clients. QUESTION 88
You have a System Center 2012 Configuration Manager environment.
You create a deployment package to deploy software updates to a collection of client computers with a deployment schedule of As soon as possible.
The Software Update Home Page indicates one installation failure for the package.
You need to view information about the installation failure.
Which log file should you view? A. SrcUpdateMgr.log
B. WUSSyncXML.log
C. SmsWusHandler.log
D. WindowsUpdate.log Answer: D QUESTION 89
You have a System Center 2012 Configuration Manager environment.
You have an application named App1.
You modify the Package Access account on the App1 software package to prevent read access for all users. Users are still able to access the package.
You need to ensure that users cannot read the package, and minimize bandwidth utilization. What should you do? A. Copy the package to all distribution points.
B. Refresh the package on all distribution points.
C. Update all distribution points with a new package source version.
D. Delete and re-create the software package. Answer: B QUESTION 90
You have a System Center 2012 Configuration Manager environment.
You deploy a site server named Lab1 to use for Pre-boot Execution Environment (PXE) installations on client computers in your training room. Administrators from other departments report that they are being prompted for PXE installations that should be available to only the client computers in your training room.
You need to ensure that only the client computers in your training room receive the PXE installations from Lab1.
What should you do? A. Modify the Broadcast Address scope option on the DHCP server.
B. Modify the Static Route option on the DHCP server.
C. Modify the Boot Server Host Name scope option on the DHCP server.
D. Publish the PXE server by using a fully qualified domain name (FQDN). Answer: C
2016 Braindump2go Valid Microsoft 70-243 Exam Study Materials: 1.| Latest Braindump2go 154q 70-243 PDF and 70-243 VCE Dumps: http://www.braindump2go.com/70-243.html [100% Exam Pass Guaranteed!]
2.| New Braindump2go 70-243 Exam Questions PDF - Google Drive: https://drive.google.com/folderview?id=0B9YP8B9sF_gNeFNybGdGYU9wQVU&usp=sharing
3.| More Braindump2go 70-243 Dumps - From 2015 to 2016 - Google Drive: https://drive.google.com/folderview?id=0B75b5xYLjSSNfkdreTRTTVpZRTBaMmMtbUFuU0RnNzBWNDYyOXNlUndGUEhzOTVabkFzdEk&usp=sharing
|

