[July-2022]Braindump2go 400-007 Exam Dumps PDF 400-007 160Q Free Offer[Q54-Q75]
July/2022 Latest Braindump2go 400-007 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 400-007 Real Exam Questions! QUESTION 54
You were tasked to enhance the security of a network with these characteristics:
- A pool of servers is accessed by numerous data centers and remote sites
- The servers are accessed via a cluster of firewalls
- The firewalls are configured properly and are not dropping traffic
- The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology should you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers? A. Poison certain subnets by adding static routes to Null0 on the core switches connected to the pool of servers.
B. Deploy uRPF strict mode.
C. Limit sources of traffic that exit the server-facing interface of the firewall cluster with ACLs.
D. Deploy uRPF loose mode Answer: C QUESTION 55
A network architect must redesign a service provider edge, where multiservice and multitenant PEs are currently present.
Which design feature should be minimized in the new design to achieve reliability? A. bridging
B. fate sharing
C. redundancy
D. unicast overlay routing Answer: B QUESTION 56
You are designing a network running both IPv4 and IPv6 to deploy QoS.
Which consideration is correct about the QoS for IPv4 and IPv6? A. IPv4 and IPv6 traffic types can use use queuing mechanisms such as LLQ, PQ and CQ.
B. IPv6 packet classification is only available with process switching, whereas IPv4 packet classification is available with both process switching and CEF.
C. IPv6 and IB/4 traffic types can use a single QoS policy to match both protocols
D. Different congestion management mechanisms need to be used for IPv4 and IPv6 traffic types Answer: C QUESTION 57
A company plans to use BFD between its routers to detect a connectivity problem inside the switched network.
An IPS is transparently installed between the switches.
Which packets shold the IPS forward for BFD to work under all circumstances? A. Fragmented packet with the do-not-fragment bit set
B. IP packets with broadcast IP source addresses
C. IP packets with the multicast IP source address
D. IP packet with the multicast IP destination address
E. IP packets with identical source and destination IP addresses
F. IP packets with the destination IP address 0.0.0.0. Answer: E QUESTION 58
A Tier-3 Service Provider is evolving into a Tier-2 Service Provider due to the amount of Enterprise business it is receiving.
The network engineers are re-evaluating their IP/MPLS design considerations in order to support duplicate/overlapping IP addressing from their Enterprise customers within each Layer3 VPN.
Which concept would need to be reviewed to ensure stability in their network? A. Assigning unique Route Distinguishers
B. Assigning unique Route Target ID'S
C. Assigning unique IP address space for the Enterprise NAT/Firewalls
D. Assigning unique VRF ID's to each L3VPN Answer: A QUESTION 59
Which three Cisco products are used in conjunction with Red Hat to provide an NFVi solution? (Choose three.) A. Cisco Prime Service Catalog
B. Cisco Open Virtual Switch
C. Cisco Nexus switches
D. Cisco UCS
E. Cisco Open Container Platform
F. Cisco Virtual Network Function Answer: CDF QUESTION 60
What are two key design principles when using a hierarchical core-distribution-access network model? (Choose two ) A. A hierarchical network design model aids fault isolation
B. The core layer is designed first, followed by the distribution layer and then the access layer
C. The core layer provides server access in a small campus.
D. A hierarchical network design facilitates changes
E. The core layer controls access to resources for security Answer: AD QUESTION 61
A Service Provider is designing a solution for a managed CE service to a number of local customers using a single CE platform and wants to have logical separation on the CE platform using Virtual Routing and Forwarding (VRF) based on IP address ranges or packet length.
Which is the most scalable solution to provide this type of VRF Selection process on the CE edge device? A. Static Routes for Route Leaking
B. Policy Based Routing
C. OSPF per VRF Instance
D. Multi-Protocol BGP Answer: B QUESTION 62
An MPLS service provider is offering a standard EoMPLS-based VPLS service to CustomerA providing Layer 2 connectivity between a central site and approximately 100 remote sites.
CustomerA wants to use the VPLS network to carry its internal multicast video feeds which are sourced at the central site and consist of 20 groups at Mbps each.
Which service provider recommendation offers the most scalability? A. EoMPLS-based VPLS can carry multicast traffic in a scalable manner
B. Use a mesh of GRE tunnels to carry the streams between sites
C. Enable snooping mechanisms on the provider PE routers.
D. Replace VPLS with a Layer 3 MVPN solution to carry the streams between sites Answer: D QUESTION 63
What best describes the difference between Automation and Orchestration? A. Automation refers to an automatic process for completing a single task and Orchestration refers to assembling and coordinating a set of tasks and conditions.
B. Automation describes a hands-off configuration process while Orchestration refers to sets of automation tasks that require the network administrator to coordinate
C. Automation refers to an automatic process for completing multiple tasks with conditions and Orchestration refers to executing tasks in parallel.
D. Automation refers to scripting languages (Python. Ansible etc.) and Orchestration refers to commercial products that control configuration deployment Answer: A QUESTION 64
A customer asks you to perform a high level review of their upcoming WAN refresh for remote sites.
The review is specially focused on their retail store operations consisting of 500+ locations connected via mutlipoint IPsec VPN solution.
Which routing protocol would be valid but would also be the most restrictive for the expansion of this deployment model? A. EIGRP
B. IS-IS
C. OSPF
D. BGP Answer: B QUESTION 65
As part of a new network design documentation, you are required to explain the reason for choosing cisco FabricPath for Layer 2 loop avoidance.
Which two elements help Cisco FabricPath mitigate Layer 2 loops if they happen in the Layer 2 MP network? (Choose two) A. MAC tunneling
B. IS-IS multipath
C. RPF check
D. TTL header Answer: CD QUESTION 66
Which design benefit of PortF ast is true? A. PortFast does not generate a spanning tree topology change hen a station on a port is connected or disconnected
B. PortFast disables spanning tree on the port, which puts the port into the forwarding state immediately after it is connected
C. PortFast allows small, unmanaged switches to be plugged into ports of access switches without risking switch loops
D. PortFast detects one-way communications on the physical port, which prevents switch loops
E. PortFast prevents switch loops that are caused by a unidirectional point to point link condition on Rapid PVST+ and MST
F. PortFast prevents switched traffic from traversing suboptimal paths on the network Answer: A QUESTION 67
You are a network designer and you must ensure that the network you design is secure.
How do you plan to prevent infected devices on your network from sourcing random DDoS attacks using forged source address? A. ACL based forwarding
B. unicast RPF loose mode
C. unicast RPF strict mode
D. ACL filtering by destination Answer: C QUESTION 68
Which protocol does an SD-Access wireless Access Point use for its fabric data plane? A. GRE
B. MPLS
C. VXLAN
D. LISP
E. CAPWAP Answer: C QUESTION 69
Refer to the exhibit. AJI links are P2P Layer 3. A high availability application is synchronizing data between host A and host B.
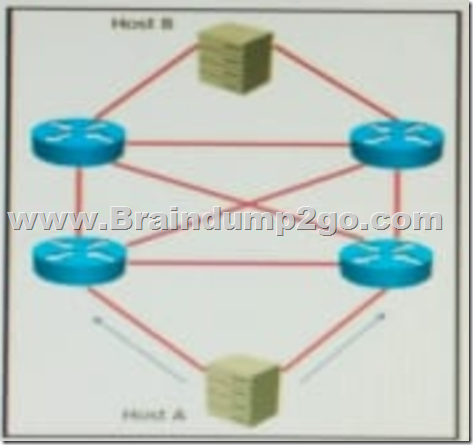
To increase chance of delivery the same data is sent twice from host A on two different NICs toward the two NICs on host B.
Which solution must be deployed in the network to ensure that any failure in the network does not trigger data loss on host B? A. EIGRP with feasible successors
B. BFD
C. IP Fast Reroute
D. Static routes Answer: C QUESTION 70
Which encoding format does cisco ios XE software support for NETCONF? A. It supports HTML encoding for NETCONF
B. It supports YAML encoding for NETCONF
C. It supports XML encoding for NETCONF
D. It supports JSON encoding for NETCONF Answer: C QUESTION 71
Which two design solutions ensure sub 50 msec of the convergence time after a link failure in the network? (Choose two) A. BFD
B. Ti-LFA
C. minimal BGP scan time
D. MPLS-FRR
E. IGP fast hello Answer: BD QUESTION 72
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated? A. VTP domain
B. VTP password
C. STP type
D. VLAN ID Answer: D QUESTION 73
Refer to the exhibit. A new high availability DB sever cluster is installed in the network.
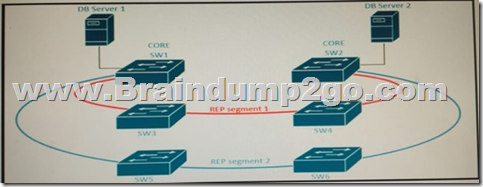
These two servers require high bandwidth and low latency Layer 2 connectivity for database replication.
Which solution supports these requirements? A. Add two new links between SW1 and SW2 configured as LACP trunk with STP
B. Add secondary links to REP segments 1 and 2
C. Add two new links between SW1 and SW2 configured as REP segment 3
D. Add two new links between SW1 and SW2 configured as REP segments 1 and 2 respectively Answer: C QUESTION 74
VPLS is implemented in a Layer 2 network with 2000 VLANs.
What is the primary concern to ensure successful deployment of VPLS? A. Flooding is necessary to propagate MAC address reachability information
B. PE scalability
C. The underlying transport mechanism
D. VLAN scalability Answer: B QUESTION 75
Which option is a fate-sharing characteristic in regards to network design? A. A failure of a single element causes the entire service to fail
B. It protects the network against failures in the distribution layer
C. It acts as a stateful forwarding device
D. It provides data sequencing and acknowledgment mechanisms Answer: A
Resources From:1.2022 Latest Braindump2go 400-007 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/400-007.html 2.2022 Latest Braindump2go 400-007 PDF and 400-007 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1wV28HLjscHjQ8TOrCglIRRU5nn6jytDd?usp=sharing 3.2021 Free Braindump2go 400-007 Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/400-007-Dumps(46-76).pdf
https://www.braindump2go.com/free-online-pdf/400-007-PDF(77-90).pdf
https://www.braindump2go.com/free-online-pdf/400-007-PDF-Dumps(1-20).pdf
https://www.braindump2go.com/free-online-pdf/400-007-VCE(21-45).pdf
https://www.braindump2go.com/free-online-pdf/400-007-VCE-Dumps(91-110).pdf Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!
|

