[Jan-2017-New]100% Success-Braindump2go 400-101 PDF and 400-101 VCE Dumps 150q Instant Download
2017 Jan. New 400-101 PDF and 400-101 VCE Dumps Released!
1.|New 400-101 Exam Dumps (PDF & VCE) 150Q&As Download:
http://www.braindump2go.com/400-101.html
2.|New 400-101 Exam Questions & Answers
https://1drv.ms/f/s!AvI7wzKf6QBjbvGwkk05I3Ao_U4 QUESTION 1
Which statement about Cisco StackWise technology is true? A. All switches in a stack share configuration and routing information to behave as a single unit
B. Removing switches can affect stack performance
C. Only the master switch acts as a forwarding processor
D. Every switch in a stack has its own independent ...configuration file, which enables it to become the stack master if the previous master fails Answer: A
Explanation:
Configuration and routing information is shared by every switch in the stack, creating a single switching unit.
http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-3750-series-switches/prod_white_paper09186a00801b096a.html QUESTION 2
Which feature can mitigate hung management sessions? A. Control Plane Policing
B. the service tcp-keepalives-in and service tcp-keepalives-out command
C. the service tcp-small servers command
D. vty line ACLs Answer: B QUESTION 3
Which option is an example of SaaS? A. Google Apps
B. Amazon AWS
C. Google App Engine
D. Microsoft Azure Answer: A QUESTION 4
How does an IPv6 host automatically generate a global address? A. It prepends its interface identifier to the network prefixes contained in Router Advertisement messages.
B. It appends its interface identifier to the network prefixes contained in Router Advertisement messages.
C. It appends its interface identifier to the network prefixes contained in Router Solicitation messages.
D. It prepends its interface identifier to the network prefixes contained in Router Solicitation messages. Answer: B QUESTION 5
Which two commands should you enter to enable IP Source Guard with IP and MAC address filtering?(Choose two) A. ip verify source tracking
B. switchport port-security
C. ip verify unicast source
D. ip verify source
E. ip verify source port-security Answer: AE QUESTION 6
Which option describes a difference between Ansible and Puppet? A. Ansible is client-server based, and Puppet is not.
B. Ansible requires an agent, and Puppet does not.
C. Ansible is Python based, and Puppet is Ruby based.
D. Ansible autonates repetitive tasks, and Puppet allows you to run plain ssh command. Answer: C QUESTION 7
What is the default behavior for a manual summary route when a component route of the summary disappears? A. Regardless of the metric if the componnent route,the metric of the summary is unchanged in order to keep stability.
B. If the component route previously had the best composite metric ,the same summary metric is retained for stability.
C. If the component route previously had the best composite metric ,the metric of the summary changes to the next-best composite metric.
D. if the component route previously did not have the best composite metric,the summary metric is updated,and updates are sent to peers. Answer: C QUESTION 8
What are the two variants of NTPv4? (Choose two.) A. client/server
B. broadcast
C. multicast
D. asymmetric
E. unicast Answer: AB QUESTION 9
For what reason might you choose to use an SVTI interface instead of a crypto map on a tunnel interface? A. SVTIs support dynamic routing protocols without GRE headers.
B. SVTIs can support multiple IPSec SAs.
C. SVTIs can carry non-IP traffic.
D. SVTIs support CEF-switched traffic shaping. Answer: A QUESTION 10
Refer to the exhibit. Which two statements about the output are true?(Choose two)
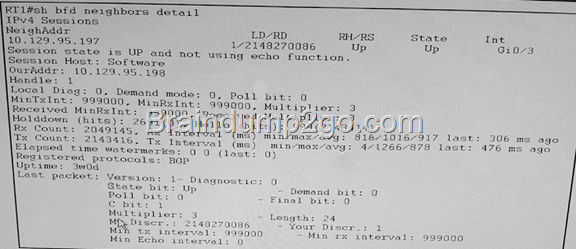 A. BFD last failed 476ms ago on interface GigabitEthernet 0/3.
B. BGP on RT1 has negotiated the BFD capability with its peer.
C. BFD is active on interface GigabitEthernet0/3 and is using ICMP.
D. BFD is active on interface GigabitEthernet0/3 and is using UDP.
E. BFD is active for BGP on RT1 Answer: BE QUESTION 11
Which two statements about PPP PAP are true?(Choose two) A. It requires two-way authentication.
B. It can protect against playback attacks.
C. It is supported only on synchronous interfaces.
D. It is vulnerable to trial-and error attacks.
E. Login attempts are controlled by the remote node. Answer: DE QUESTION 12
Refer to the exhibit. What is the PHB class on this flow?
A. none
B. CS4
C. EF
D. AF21 Answer: B QUESTION 149
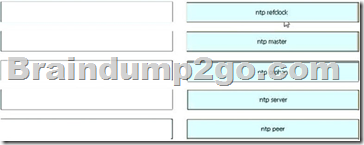
Drag and Drop Question
Drag each NTP command on the left to its effect on the right.
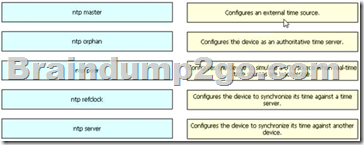
Answer:
!!!RECOMMEND!!! 1.Braindump2go|New 400-101 Exam Dumps (PDF & VCE) 150Q&As Download:
http://www.braindump2go.com/400-101.html
2.Braindump2go|New 400-101 Study Guide:
YouTube Video: YouTube.com/watch?v=2-TxDifaj5A
|


