[Full-Version!]Braindump2go Cisco 400-251 (CCIE Security) Exam Dumps Free Download[Question36-Question45]
2017 CISCO Official News: 350-018 Exam is Replaced by 400-251 Written Exam Now!
2017 New 400-251: CCIE Security Written Exam v5.1 PDF and VCE Dumps Just Released Today by Braindump2go.com!
1.|2017 NEW 400-251 Written Exam Dumps (PDF & VCE) 1106Q&As Download:
http://www.braindump2go.com/400-251.html
2.|2017 NEW 400-251 Written Exam Questions & Answers:
http://www.braindump2go.com/400-251.html QUESTION 36
On which two protocols is VNC based? (Choose two) A. Rdesktop
B. UDP
C. RFB
D. Terminal Services Client
E. CoRD
F. TCP Answer: CF QUESTION 37
How can the tail drop algorithem support traffic when the queue is filled? A. It drop older packet with a size of 64 byts or more until queue has more traffic
B. It drop older packet with a size of less than 64 byts until queue has more traffic
C. It drops all new packets until the queue has room for more traffic
D. It drops older TCP packets that are set to be redelivered due to error on the link until the queue has room for more traffic. Answer: C QUESTION 38
Drag and Drop Question
Drag each step in the cisco PRIST response to incidents and vulnerability involving cisco product on the left into the correct order on the right.

Answer:
 QUESTION 39
Which two statements about the 3DES encryption protocol are true? (Choose two) A. It can operate in the Electronic Code Book and Asymmetric Block Chaining modes.
B. Its effective key length is 168 bits.
C. It encrypts and decrypts data in three 64-bit blocks with an overall key length of 192 bits.
D. The algorithm is most efficient when it is implemented in software instead of hardware.
E. It encrypts and decrypts data in three 56-bit blocks with an overall key length of 168 bits.
F. Its effective key length is 112 bits. Answer: EF QUESTION 40
You want to enable users in your company's branch offices to deploy their own access points using WAN link from the central office, but you are unable to a deploy a controller in the branch offices. What lightweight access point wireless mode should you choose? A. TLS mode
B. H-REAP mode
C. Monitor mode
D. REAP mode
E. Local mode Answer: B QUESTION 41
Refer to the exhibit. Which two effect of this configuration are true ? (Choose two)
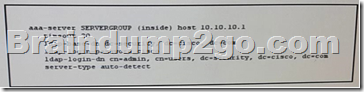 A. The Cisco ASA first check the user credentials against the AD tree of the security.cisco.com.
B. The Cisco ASA use the cisco directory as the starting point for the user search.
C. The AAA server SERVERGROUP is configured on host 10.10.10.1 with the timeout of 20 seconds.
D. The Cisco ASA uses the security account to log in to the AD directory and search for the user cisco.
E. The Cisco ASA authentication directly with the AD server configured on host 10.10.10.1 with the timeout of 20 second.
F. The admin user is authenticated against the members of the security.cisco.com group. Answer: CF QUESTION 42
Which object table contains information about the clients know to the server in Cisco NHRP MIB implementation? A. NHRP Cache Table
B. NHRP Client Statistics Table
C. NHRP Purge Request Table
D. NHRP Server NHC Table Answer: D QUESTION 43
What is the default communication port used by RSA SDI and ASA ? A. UDP 500
B. UDP 848
C. UDP 4500
D. UDP 5500 Answer: D QUESTION 44
when a client tries to connect to a WLAN using the MAC filter (RADIUS server), if the client fails the authentication, what is the web policy used tofallback authentication to web authentication ? A. Authentication
B. Passthrough
C. Conditional Web Redirect
D. Splash Page Web Redirect
E. On MAC Filter Failure Answer: E QUESTION 45
Refer the exhibit. Which of the following is the correct output of the above executed command?
 A. 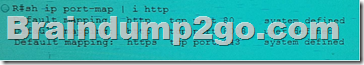
B. 
C. 
D. ![image_thumb[11] image_thumb[11]](http://examgod.com/bdimages/Full-VersionQuestion36-Question45_A735/image_thumb11_thumb.png) Answer: C
!!! RECOMMEND!!! 1.|2017 NEW 400-251 Exam Dumps (PDF & VCE) 1106Q&As Download:
http://www.braindump2go.com/400-251.html
2.|2017 NEW 400-251 Study Guide Video:
YouTube Video: YouTube.com/watch?v=GSXnXKIh834
" href="https://youtu.be/GSXnXKIh834"> YouTube Video: YouTube.com/watch?v=GSXnXKIh834
|







![image_thumb[11] image_thumb[11]](http://examgod.com/bdimages/Full-VersionQuestion36-Question45_A735/image_thumb11_thumb.png)