Free Download PDF & VCE Format Microsoft 70-689 Dumps With New Changed Questions from Braindump2go (11-20)
Get Prepared with fully updated Microsoft 70-689 Real Exam Questions and Accurate Answers for 70-689 Exam Dumps. Braindump2go IT experts review the 70-689 newly added qustions and suggest Correct Microsoft 70-689 Exam Questions Answers in Real Time. 100% Pass easily! Vendor: Microsoft
Exam Code: 70-689
Exam Name: Microsoft Upgrading Your Skills to MCSA Windows 8.1 
QUESTION 11
You administer a group of 10 client computers that run Windows 8.
The client computers are members of a local workgroup.
Employees log on to the client computers by using their Microsoft accounts.
The company plans to use Windows BitLocker Drive Encryption.
You need to back up the BitLocker recovery key.
Which two options can you use? (Each correct answer presents a complete solution. Choose two.) A. Save the recovery key to a file on the BitLocker-encrypted drive.
B. Save the recovery key in the Credential Store.
C. Save the recovery key to SkyDrive.
D. Print the recovery key. Answer: AD
Explanation:
One of the new features in Windows 8 for BitLocker is the ability to backup your BitLocker recovery key to a Microsoft account. During the process before encryption begins, a user is prompted for a location to make a backup copy of the recovery key. Save to your Microsoft account has been added along with save to a file and print the recovery key. 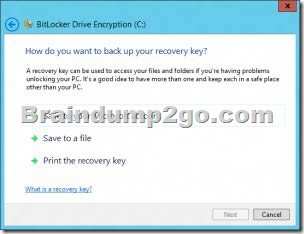
QUESTION 12
You administer Windows 8 computers in your company network.
You install a new video driver.
The computer will not start properly after restart.
You are able to enter Safe Mode with Command Prompt.
You need to be able to start normally.
You also need to ensure that user data is not lost.
What should you do?
A. Run the rstrui.exe command.
B. Roll back the driver.
C. Turn on File History.
D. Create a restore point. Answer: A QUESTION 13
You administer Windows 8 Pro client computers in your company network.
You need to configure a backup and recovery solution that meets the following requirements:
- Recovers the system if it doesn't start.
- Recovers the system if the hard drive fails.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.) A. Turn on File History.
B. Create a storage space.
C. Configure system protection.
D. Create a system repair disk.
E. Create a system image backup. Answer: DE
Explanation:
- In the event that you are unable to start Windows or wish to restore your hard drives to a previous backup you can use the System Image Recovery program from the Windows 7 or Windows 8 Recovery Environment.
- You should create a system repair disk, which can be used to boot your PC and restore it using the system image backup, in the event of a hard drive issue or other hardware failure.
Incorrect:
C: System protection is a feature that regularly creates and saves information about your computer's system files and settings. System protection also saves previous versions of files that you've modified. It saves these files in restore points, which are created just before significant system events, such as the installation of a program or device driver.
They're also created automatically once every seven days if no other restore points were created in the previous seven days, but you can create restore points manually at any time. QUESTION 14
A company has an Active Directory Domain Services (AD DS) domain.
All client computers run Windows 7.
You plan to upgrade the client computers to Windows 8 Pro.
You need to choose the methods that do not require the manual entry of a product key during the upgrade.
Which two methods should you choose? (Each correct answer presents a complete solution. Choose two.) A. Use the Volume Activation Management Tool.
B. Use the Microsoft Deployment Toolkit.
C. Use the Windows 8 online upgrade tool.
D. Create a catalog (.clg) file by using Windows System Image Manager (SIM). Answer: AB
Explanation:
A: Volume Activation Management Tool (VAMT) 2.0 is a managed MMC plug-in.
VAMT uses Windows Management Instrumentation (WMI) to configure managed systems.
A convenient command line interface (CLI) allows automated, scheduled VAMT tasks without UI interaction. Using the VAMT console, administrators can perform many activation-related tasks on remote computers:
Manage product keys obtained from the Volume Licensing Service Center (VLSC) or other sources including retail and Microsoft subscription programs such as MSDN, TechNet and partner programs
- and product activations using those keys.
Activate remote systems using Key Management Service (KMS), Multiple Activation Key (MAK) or retail activation methods.
Perform disconnected proxy activation and reactivation of systems without each system having to connect with Microsoft activation services individually.
Assist with license compliance by enabling IT administrators to monitor system license state, including whether systems are licensed and running genuine Windows or Office.
B: Deploy Windows and Office 2010 with Microsoft Deployment Toolkit 2012 Update 1.
MDT is the recommended process and toolset for automating desktop and server deployment. MDT provides you with the following benefits:
Unified tools and processes, including a set of guidance, for deploying desktops and servers in a common deployment console.
Reduced deployment time and standardized desktop and server images, along with improved security and ongoing configuration management. QUESTION 15
You administer computers in your company network.
All computers in the network belong to a single Active Directory Domain Services (AD DS) domain.
The network includes Windows Server 2012 servers located in a perimeter network.
You add a new Windows 8 computer to the perimeter network.
You enable only Remote Desktop access to the Windows 8 computer from other computers located outside the perimeter network.
You need to use the Windows 8 computer to manage the Windows servers in the perimeter network.
What should you do? A. Add the Windows 8 computer as a Trusted Host to the servers.
B. Enable PowerShell Remoting on the Windows 8 computer.
C. Add the Windows 8 computer as a Trusted Host to computers outside the perimeter network.
D. Install Remote Server Administration Tools for Windows 8 (RSAT) on the Windows 8
computer. Answer: B QUESTION 16
A company has client computers that run Windows 8.
Each computer has two hard drives.
You need to create a dynamic volume on each computer to support the following features:
- Fault tolerance
- Fast write performance
What kind of dynamic volume should you create? A. Striped volume
B. Spanned volume
C. RAID 5 volume
D. Mirrored volume Answer: D QUESTION 17
You administer Windows 8 Enterprise computers in your company's Active Directory Domain Services (AD DS) domain.
Your company uses several peripheral devices.
The drivers for these devices are not available on Windows Update.
You need to ensure that the drivers install when users connect these devices to their computers. What should you do? A. For the Group Policy setting Prioritize all digitally signed drivers equally during the driver
ranking and selection process, select Disabled.
B. From Device Manager, find the detected scanner device and select Update Driver.
C. Add the following registry key to the computers:
HKEY_LOCAL_MACHINE/Software/Microsoft/Windows/Current Version/DevicePath.
Add °/osystemroot%inf and the UNC path to the drivers share.
D. For the Group Policy setting Configure driver search locations, select Enabled.
Make the drivers available on the UNC path to the driver's share. Answer: C QUESTION 18
A company has client computers that run Windows 8.
Each computer has two hard drives.
You need to create a dynamic volume on each computer that maximizes write performance with data fault tolerance.
Which kind of dynamic volume should you create? A. Striped Volume
B. RAID 5 Volume
C. Spanned Volume
D. Mirrored Volume Answer: D QUESTION 19
A company network contains two workgroups named Workgroup1 and Workgroup2.
Workgroup1 contains computers that run Windows 7.
Workgroup2 contains computers that run Windows 8.
You run the Enable-PSRemoting Windows PowerShell cmdlet on the Workgroup2 computers.
You need to ensure that administrators can manage the Workgroup1 computers from the Workgroup2 computers by using Windows PowerShell Remoting.1
Which two actions should you perform? (Each correct answer presents part of the complete solution. Choose two.) A. Install Windows PowerShell 2.0 on the Workgroup1 computers.
B. Run the winrm quickconfig command on the Workgroup2 computers.
C. On the Workgroup1 computers, add the Workgroup2 computers to the trusted hosts in
Windows Remote Management (WinRM).
D. Run the winrrn quickconfig command on the Workgroup1 computers.
E. On the Workgroup2 computers, add the Workgroup1 computers to the trusted hosts in
Windows Remote Management (WinRM). Answer: BC
Explanation:
B: If you cannot connect to a remote host, verify that the service on the remote host is running and is accepting requests by running the following command on the remote host:
winrm quickconfig
This command analyzes and configures the WinRM service.
C: To enable authentication, you need to add the remote computer to the list of trusted hosts for the local computer in WinRM. To do so, type:
winrm s winrm/config/client '@{TrustedHosts="RemoteComputer"}'
Here, RemoteComputer should be the name of the remote computer, such as:
winrm s winrm/config/client '@{TrustedHosts="CorpServer56"}'
Incorrect:
Not A: The Windows PowerShell remoting features are supported by the WS-Management protocol and the Windows Remote Management (WinRM) service that implements WS-Management in Windows.
Computers running Windows 7 and later include WinRM 2.0 or later.
On computersrunning earlier versions of Windows, you need to install WinRM 2.0 or later as appropriate and if supported.
Reference: Enable and Use Remote Commands in Windows PowerShell QUESTION 20
A computer that runs Windows B has two hard disk drives.
The user stores data files in specific storage locations outside of the standard libraries on both drives.
File search results are delayed.
You need to return relevant search results more quickly.
What should you do? A. Remove all directories from indexed locations.
B. Add the specific storage locations to indexed locations.
C. Allow indexing of file contents in non-indexed locations.
D. Add encrypted files to the index. Answer: B
Braindump2go Promise All 70-689 Questions and Answers are the Latest Updated,we aim to provide latest and guaranteed questions for all certifications.You just need to be braved in trying then we will help you arrange all left things! 100% Pass All Exams you want Or Full Money Back! Do yo want to have a try on passing 70-689? 
http://www.braindump2go.com/70-689.html
|


