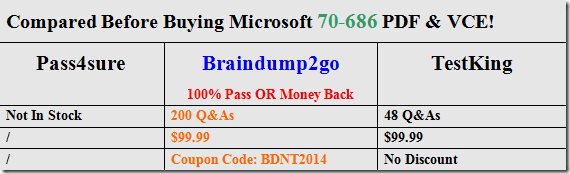
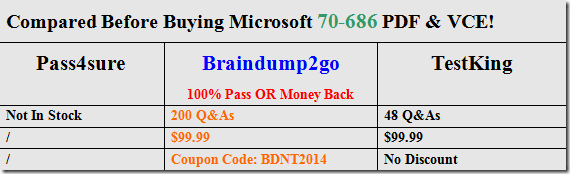
Braindump2go Updates Microsoft 70-686 Exam Dumps Questions, adds some new changed questions from Microsoft Official Exam Center. Want to know 2015 70-686 Exam test points? Download the following free Braindump2go Latest Exam Questions Today!
Vendor: Microsoft
Exam Code: 70-686
Exam Name: Pro: Windows 7, Enterprise Desktop Administrator
QUESTION 1
Your company has 1,000 client computers that run Windows 7 Enterprise.
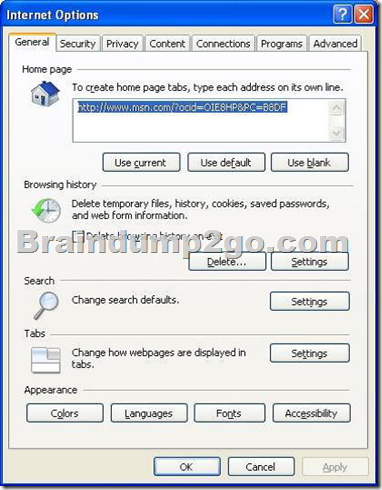
You need to ensure that users cannot bypass or disable Internet Explorer logging.
What should you do?
A. Set the Disable the Advanced Page state to Enabled, and set the Turn off InPrivate Browsing
state to Enabled.
B. Set the Turn off InPrivate Filtering state to Enabled, and set the Disable the General Page
state to Enabled.
C. Set the Turn off InPrivate Browsing state to Enabled, and set the Disable the General Page
state to Enabled.
D. Set the Disable the General Page state to Enabled, and set the Disable the Advanced Page
state to Enabled.
Answer: C
Explanation:
InPrivate Browsing in Internet Explorer 8 helps prevent one’s browsing history, temporary Internet files, form data, cookies, and usernames and passwords from being retained by the browser, leaving no easily accessible evidence of browsing or search history.
http://en.wikipedia.org/wiki/Internet_Explorer_8
hints:
run IE InPrivate Browsing will not keep any history or logging.
General Page able to clear IE history untitled
QUESTION 2
All client computers in your network run Windows 7 with default firewall settings.
You have a server-based application that requires an agent to be installed on all client computers.
You need to use Group Policy to allow the application to initiate installation of the agent on all client computers.
What should you do?
A. Create inbound program rules.
B. Create inbound port rules.
C. Create Windows service hardening rules.
D. Create connection security rules.
Answer: B
Explanation:
hints:
software havent install, so unable to block program
QUESTION 3
All client computers in your network run Windows 7 Enterprise.
You need to prevent all standard user accounts from running programs that are signed by a specific publisher.
What should you do?
A. Use AppLocker application control policies. Create an Executable rule.
B. Use software restriction policies. Create a hash rule.
C. Use AppLocker application control policies. Create a Windows Installer rule.
D. Use software restriction policies. Create a path rule.
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/dd759068.aspx
The AppLocker Microsoft Management Console (MMC) snap-in is organized into four areas called rule collections.
The four rule collections are executable files, scripts, Windows Installer files, and DLL files.
These collections give the administrator an easy way to differentiate the rules for different types of applications.
Rule conditions are criteria that the AppLocker rule is based on.
Primary conditions are required to create an AppLocker rule.
The three primary rule conditions are publisher, path, and file hash.
Publisher-This condition identifies an application based on its digital signature and extended attributes. The digital signature contains information about the company that created the application (the publisher). The extended attributes, which are obtained from the binary resource, contain the name of the product that the application is part of and the version number of the application.
The publisher may be a software development company, such as Microsoft, or the information technology department of your organization.
Path-This condition identifies an application by its location in the file system of the computer or on the network. AppLocker uses path variables for directories in Windows.
File hash-When the file hash condition is chosen, the system computes a cryptographic hash of the identified file.
QUESTION 4
Your network has a single domain with 1,000 client computers that run Windows 7.
You use Microsoft System Center Configuration Manager 2007 to distribute and install software applications.
All users have standard user accounts.
You plan to use Group Policy to ensure that application installation functions properly.
You need to design the User Account Control (UAC) policy.
What should you do?
A. Configure the User Account Control:
Behavior of the elevation prompt for standard users setting to be Prompt for credentials.
B. Configure the User Account Control:
Only elevate executables that are signed and validated setting to be Enabled.
C. Configure the User Account Control:
Detect application installations and prompt for elevation setting to be Disabled.
D. Configure the User Account Control:
Detect application installations and prompt for elevation setting to be Enabled.
Answer: C
Explanation:
User Account Control: Detect application installations and prompt for elevation
The User Account Control: Detect application installations and prompt for elevation policy setting controls the behavior of application installation detection for the computer.
The options are:
Enabled. (Default for home) When an application installation package is detected that requires elevation of privilege, the user is prompted to enter an administrative user name and password. If the user enters valid credentials, the operation continues with the applicable privilege.
Disabled. (Default for enterprise) Application installation packages are not detected and prompted for elevation. Enterprises that are running standard user desktops and use delegated installation technologies such as Group Policy Software Installation or Systems Management Server (SMS) should disable this policy setting. In this case, installer detection is unnecessary.
http://technet.microsoft.com/en-us/library/dd851376.aspx
QUESTION 5
Your network has 1,000 client computers that run Windows 7.
You need to install an application, in the Local System account context, on the client computers.
What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
A. Configure a logon script.
B. Configure a startup script.
C. Configure a shutdown script.
D. Configure a logoff script.
Answer: BC
QUESTION 6
You are planning to deploy Windows 7 to all client computers in your network.
You need to ensure that domain administrators can manage domain Group Policy objects (GPOs) from their Windows 7 computers.
What should you provide to the domain administrators?
A. Local Group Policy Editor
B. GPOAccelerator Tool
C. Remote Server Administration Tools
D. Administration Tools Pack
Answer: C
Explanation:
Group Polices were modified using the Group Policy Edit tool that was integrated with Active Directory Users and Computers Microsoft Management Console (MMC) snap-in, but it was later split into a separate MMC snap-in called the Group Policy Management Console (GPMC).
The GPMC is now a user component in Windows Server 2008 and Windows Server 2008 R2 and is provided as a download as part of the Remote Server Administration Tools for Windows Vista and Windows 7.
http://en.wikipedia.org/wiki/Group_Policy
QUESTION 7
Your network has a single domain with 1,000 client computers that run Windows 7.
Users frequently copy data from their computers to removable drives.
You need to ensure that data that is copied to removable drives is protected.
What should you do?
A. Use Encrypting File System (EFS)
B. Enable Trusted Platform Module (TPM) hardware on all client computers
C. Use Active Directory Rights Management Services
D. Configure a Group Policy to enforce the use of BitLocker To Go
Answer: D
Explanation:
BitLocker to Go extends BitLocker data protection to USB storage devices, enabling them to be restricted with a passphrase. In addition to having control over passphrase length and complexity, IT administrators can set a policy that requires users to apply BitLocker protection to removable drives before being able to write to them.
http://www.microsoft.com/en-us/windows/enterprise/products-and-technologies/windows-7/features.aspx#bitlocker
QUESTION 8
Your network has a single domain with 1,000 client computers that run Windows 7.
A large number of software installation scripts are configured to run on the client computers.
You need to recommend a Group Policy setting to allow users to log on to their computers as soon as possible at first boot.
What should you recommend?
A. Configure the Run logon scripts synchronously setting to be Enabled.
B. Configure the Run logon scripts synchronously setting to be Disabled.
C. Configure the Run startup scripts asynchronously setting to be Enabled.
D. Configure the Run startup scripts asynchronously setting to be Disabled.
Answer: C
Explanation:
Run logon scripts synchronously
Description
Directs the system to wait for logon scripts to finish running before it starts the Windows Explorer interface program and creates the desktop.
If you enable this policy, Windows Explorer does not start until the logon scripts have finished running. This setting assures that logon script processing is complete before the user starts working, but it can delay the appearance of the desktop.
If you disable this policy or do not configure it, the logon scripts and Windows Explorer are not synchronized and can run simultaneously.
Run startup scripts asynchronously
Description
Lets the system run startup scripts simultaneously.
Startup scripts are batch files that run before the user is invited to log on. By default, the system waits for each startup script to complete before it runs the next startup script.
If you enable this policy, the system does not coordinate the running of startup scripts.
As a result, startup scripts can run simultaneously.
If you disable this policy or do not configure it, a startup script cannot run until the previous script is complete.
http://msdn.microsoft.com/en-us/library/ms811602.aspx
QUESTION 9
Your company has 1,000 computers in the main office and 20 computers in store kiosks.
All the computers run Windows 7 Enterprise.
The kiosk computers do not have network connections.
The company brands the Internet Explorer program window on all computers by displaying the company logo at the left end of the title bar. The company changes its logo.
You have the following requirements:
– Display the new logo on the Internet Explorer program window title bar on the main office computers and the kiosk computers.
– Modify the search providers that are available to main office computers.
You need to define Internet Explorer settings to support the requirements.
What should you do?
A. Use the Internet Explorer Administration Kit (IEAK) to create a custom configuration-only
deployment package on the main office computers.
Create a deployment CD for the kiosk computers.
B. Use the Internet Explorer Administration Kit (IEAK) to create a custom configuration-only
deployment package on the main office computers.
Enable automatic version synchronization and specify a flash drive for the path.
Distribute the configuration package to the kiosk computers.
C. Save the logo as Logo.png and copy the file to the C:\Windows\Branding\ directory on each
kiosk computer.
Create and distribute a new OpenSearch description file for the main office computers.
D. Use the Internet Explorer Administration Kit (IEAK) to create a custom configuration-only
deployment package.
Copy the setup file to a flash drive, and distribute the file to all computers.
Answer: A
Explanation:
Hints:
Kiosk computer do not have network connections, deployment CD is needed.
QUESTION 10
You are planning to test a custom image of Windows 7 Enterprise.
You deploy the image on test computers in Toronto by using ConfigMgr.
The deployed image fails to activate.
You need to ensure that the image meets company activation requirements.
What should you do?
A. Run the Sysprep/generalize command.
B. Run the Sysprep/oobe command.
C. Modify the unattend.xml file and enter a MAK key.
D. Modify the unattend.xml file and enter a KMS key.
Answer: A
For those who feel the overwhelming anxiety before their 70-686 exam,Braindump2go Latest updated 70-686 Exam Dumps will help you Pass 100% in a short time preparation! 70-686 Exam Dumps PDF & VCE Full Version Instant Download!