[December-2021]Braindump2go SC-900 VCE and SC-900 Dumps SC-900 101Q Free Offered[Q52-Q82]
December/2021 Latest Braindump2go SC-900 Exam Dumps with PDF and VCE Free Updated Today! Following are some new SC-900 Real Exam Questions! QUESTION 52
A company wants to make use of Windows Hello for business when it comes to authentication.
Which of the following are the authentication techniques available for Windows Hello for business? Choose 3 answers from the options given below A. PIN
B. Facial Recognition
C. Email message
D. Password
E. Fingerprint recognition Answer: ABE
Explanation:
The entire purpose of Windows Hello for business is to ensure passwords are not used in the authentication process. Here uses can use other techniques for authentication via the usage of PIN's and biometric recognition.
Options C and D are incorrect since Windows Hello for Business tries to ensure that secure measures are used for the authentication process.
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview 1 QUESTION 53
Which of the following can be used to provide a secure score for the resources defined as part of your Azure account?
 A. Azure Security Center
B. Azure key Vaults
C. Azure Sentinel
D. Azure Information Protection Answer: A
Explanation:
You can accomplish this with the help of Azure Security Center
If you go to Azure Security Center, in the Overview you can see the secure score.
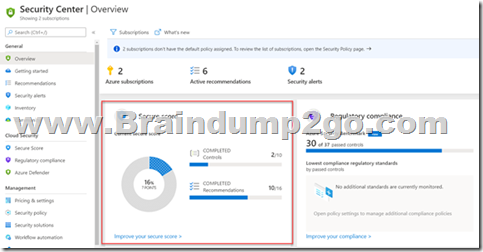
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-introduction 2 QUESTION 54
Your company has just setup an Azure subscription. They have the following requirements
- Be able to deploy a set of resources, resource groups, role assignments to a set of subscriptions.
- Be able to ensure no one can delete resources defined in a resource group named lead2pass-staging
- Ensure that all Windows Servers defined as Azure virtual machines should have the Microsoft IaaS Antimalware extension installed
Which of the following can be used for the following requirement?
- Be able to ensure no one can delete resources defined in a resource group named lead2pass-rg A. Azure Policy
B. Azure Blueprints
C. Azure AD Identity Protection
D. Azure Resource locks Answer: D
Explanation:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/lock-resources 3 QUESTION 55
You are considering the use of sensitivity labels in Microsoft 365. Can sensitivity labels can be used to encrypt the contents in documents? A. Yes
B. No Answer: A
Explanation:
When you apply a “Confidential” label to a document, the label will encrypt the content in the document.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide 28 4 QUESTION 56
You are planning on making use of the Azure Bastion service. Can you use the Azure Bastion service to restrict traffic from the Internet onto an Azure virtual machine? A. Yes
B. No Answer: A
Explanation:
You cannot use the Azure Bastion service to restrict traffic into an Azure virtual machine. For this you will need to use Network Security groups. The Azure Bastion service is used to RDP/SSH into an Azure virtual machine via the Azure portal and the browser.
Reference:
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview 5 QUESTION 57
You are looking at the capabilities of Azure Active Directory. Can you use Azure Active Directory to manage device registrations in Azure Active Directory? A. Yes
B. No Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/devices/overview 6 QUESTION 58
Your company is planning on using Azure Cloud services. Which of the following can be used to ensure that data can be read only by authorized users? A. Encryption
B. Deduplication
C. Archiving
D. Compression Answer: A
Explanation:
You can ensure data is encrypted. Then only authorized users would have the encryption key. The encryption key can then be used to decrypt and read the data.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/office-365-encryption-in-the-microsoft-cloud-overview?view=o365-worldwide 7 QUESTION 59
Your company is planning on using Azure Active Directory for the storage of identities. They want to make use of the self-service password reset feature.
Which of the following authentication methods are available for self-service password reset? Choose 3 answers from the options given below A. Email
B. A passport identification number
C. A picture message
D. Mobile app notification
E. Mobile app code Answer: ADE
Explanation:
Below are the authentication methods available for self-service password reset:
Mobile app notification
Mobile app code
Email
Mobile phone
Office phone
Security questions
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-sspr-howitworks 8 QUESTION 60
Your company wants to start making use of Azure. They are looking at different security aspects when it comes to using Azure.
Which of the following could be used for the following requirement?
- Enforce Multi-Factor authentication based on the sign-in risk A. Azure AD Identity Management
B. Azure Conditional Access
C. Azure AD Roles
D. Azure AD Connect Answer: A
Explanation:
In Azure AD Identity Protection, you can configure the Sign-in risk policy to allow access and enforce the use of Multi-Factor Authentication.
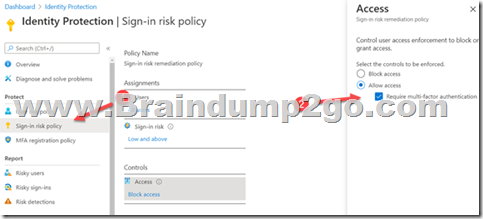
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection 9 QUESTION 61
Which of the following is a scalable, cloud-native, security information event management and security orchestration automated response solution? A. Azure Sentinel
B. Azure Security Center
C. Azure Active Directory
D. Azure AD Identity Protection Answer: A
Explanation:
You can use Azure Sentinel as a scalable, cloud-native, security information event management and security orchestration automated response solution. Azure Sentinel has the capability to ingest data from a variety of sources and performance threat monitoring on that data.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview 10 QUESTION 62
Which of the following provides advanced and intelligent protection of Azure and hybrid resources and workloads? A. Azure Defender
B. Azure Policies
C. Azure Blueprints
D. Azure Active Directory Answer: A
Explanation:
With Azure Defender , you can enable intelligent protection of your resources that are defined in Azure and also in your on-premises infrastructure.
This is an additional security feature that comes as part of Azure Security Center as shown below
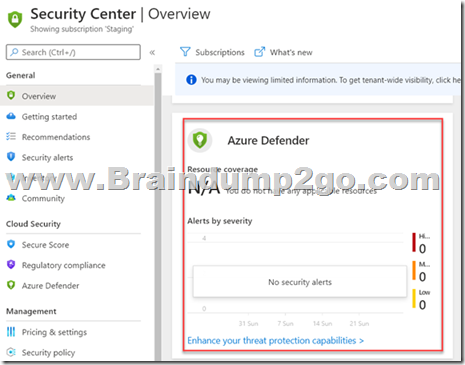
Reference:
https://docs.microsoft.com/en-us/azure/security-center/azure-defender 11 QUESTION 63
Which of the following is available for the Azure Application Gateway service that helps to protect web applications from common exploits and vulnerabilities? A. Azure Firewall
B. Azure Web Application Firewall
C. Azure Policy
D. Azure Identity Protection Answer: B
Explanation:
The Azure Web Application Firewall can be used along with the Azure Application Gateway resource to protect web applications from common exploits and vulnerabilities. It can help to protect against attacks such as SQL injection attacks or cross-site scripting attacks.
Reference:
https://docs.microsoft.com/en-us/azure/web-application-firewall/ag/ag-overview 12 QUESTION 64
You are evaluating the different services available in Azure when it comes to security. Which of the following can be accomplished with the use of the Azure Privileged Identity Managed service? A. Filter traffic to Azure virtual machines
B. Enable Multi-Factor Authentication for users based on detected sign-in risks
C. Provide just-in-time access to resource roles in Azure
D. Measure the security posture of resources defined in an Azure environment Answer: C
Explanation:
With Azure Privileged Identity Managed , you can provide just-in-time access to Azure AD roles and resource roles. Here users can request for access whenever required. And the access can be granted or denied accordingly.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure 13 QUESTION 65
You are evaluating the different discovery tools that are available with Microsoft 365. You need to map the tool that can be used for desired requirement below:
- Be able to quickly find email in Exchange mailboxes
Which of the following would you use for this requirement? A. Core eDiscovery
B. Advanced eDiscovery
C. Sensitivity labels
D. Content search Answer: D
Explanation:
The Content search tool can be used to quickly find email in Exchange mailboxes, documents in SharePoint sites and OneDrive locations.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/search-for-content?view=o365-worldwide 14 QUESTION 66
You are evaluating the different discovery tools that are available with Microsoft 365. You need to map the tool that can be used for desired requirement below:
- Provide basic capabilities on searching and exporting of content in Microsoft 365
Which of the following would you use for this requirement? A. Core eDiscovery
B. Privileged Access Management
C. Sensitivity labels
D. Content search Answer: A
Explanation:
The Core eDiscovery tool helps you to find and export content in Microsoft 365 and Office 365. You can also use the tool to place an eDiscovery hold on certain content locations.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-core-ediscovery?view=o365-worldwide 25 15 QUESTION 67
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point. A. Plan
B. Manage
C. Adopt
D. Govern
E. Define Strategy Answer: AE
Explanation:
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/overview 16 QUESTION 68
What is an example of encryption at rest? A. encrypting communications by using a site-to-site VPN
B. encrypting a virtual machine disk
C. accessing a website by using an encrypted HTTPS connection
D. sending an encrypted email Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/security/fundamentals/encryption-atrest 17 QUESTION 69
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization? A. sensitivity label policies
B. Customer Lockbox
C. information batteries
D. Privileged Access Management (PAM) Answer: C
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-barriers 18 QUESTION 70
Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point. A. fingerprint
B. facial recognition
C. PIN
D. email verification
E. security question Answer: ABC
Explanation:
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-how-it-works-authentication 19 QUESTION 71
What feature in Microsoft Defender for Endpoint provides the first line of defense against cyberthreats by reducing the attack surface? A. automated remediation
B. automated investigation
C. advanced hunting
D. network protection Answer: D
Explanation:
Network protection helps protect devices from Internet-based events. Network protection is an attack surface reduction capability.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection?view=o365-worldwide 20 QUESTION 72
Which two types of resources can be protected by using Azure Firewall? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point. A. Azure virtual machines
B. Azure Active Directory (Azure AD) users
C. Microsoft Exchange Online inboxes
D. Azure virtual networks
E. Microsoft SharePoint Online sites Answer: DE QUESTION 73
You plan to implement a security strategy and place multiple layers of defense throughout a network infrastructure.
Which security methodology does this represent? A. threat modeling
B. identity as the security perimeter
C. defense in depth
D. the shared responsibility model Answer: C
Explanation:
https://docs.microsoft.com/en-us/learn/modules/secure-network-connectivity-azure/2-what-is-defense-in-depth 21 QUESTION 74
What can you use to scan email attachments and forward the attachments to recipients only if the attachments are free from malware? A. Microsoft Defender for Office 365
B. Microsoft Defender Antivirus
C. Microsoft Defender for Identity
D. Microsoft Defender for Endpoint Answer: A
Explanation:
https://docs.microsoft.com/en-us/office365/servicedescriptions/office-365-advanced-threat-protection-service-description 22 QUESTION 75
Which feature provides the extended detection and response (XDR) capability of Azure Sentinel? A. integration with the Microsoft 365 compliance center
B. support for threat hunting
C. integration with Microsoft 365 Defender
D. support for Azure Monitor Workbooks Answer: C
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/eval-overview?view=o365-worldwide 23 QUESTION 76
What can you use to provide threat detection for Azure SQL Managed Instance? A. Microsoft Secure Score
B. application security groups
C. Azure Defender
D. Azure Bastion Answer: C QUESTION 77
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources? A. network security groups (NSGs)
B. Azure AD Privileged Identity Management (PIM)
C. conditional access policies
D. resource locks Answer: C QUESTION 78
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers? A. retention policies
B. data loss prevention (DLP) policies
C. conditional access policies
D. information barriers Answer: B
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide 24 QUESTION 79
In a Core eDiscovery workflow, what should you do before you can search for content? A. Create an eDiscovery hold.
B. Run Express Analysis.
C. Configure attorney-client privilege detection.
D. Export and download results. Answer: A
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-core-ediscovery?view=o365-worldwide 25 15 QUESTION 80
Which Microsoft portal provides information about how Microsoft manages privacy, compliance, and security? A. Microsoft Service Trust Portal
B. Compliance Manager
C. Microsoft 365 compliance center
D. Microsoft Support Answer: A
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365-worldwide 26 QUESTION 81
What can you protect by using the information protection solution in the Microsoft 365 compliance center? A. computers from zero-day exploits
B. users from phishing attempts
C. files from malware and viruses
D. sensitive data from being exposed to unauthorized users Answer: D
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide 27 QUESTION 82
What can you specify in Microsoft 365 sensitivity labels? A. how long files must be preserved
B. when to archive an email message
C. which watermark to add to files
D. where to store files Answer: C
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide 28 4
Resources From:1.2021 Latest Braindump2go SC-900 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/sc-900.html 2.2021 Latest Braindump2go SC-900 PDF and SC-900 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1lBjx9vxksSKq1-ok4CmD-HBgZND4cDno?usp=sharing 3.2021 Free Braindump2go SC-900 Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/SC-900-PDF(42-62).pdf
https://www.braindump2go.com/free-online-pdf/SC-900-PDF-Dumps(1-20).pdf
https://www.braindump2go.com/free-online-pdf/SC-900-VCE(63-85).pdf
https://www.braindump2go.com/free-online-pdf/SC-900-VCE-Dumps(21-41).pdf Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!
|



