Braindump2go Shares the Latest Free Official Microsoft 70-411 Exam Training Questions and Answers (81-90)
MICROSOFT OFFICIAL: New Updated 70-411 Exam Questions from Braindump2go 70-411 PDF Dumps and 70-411 VCE Dumps! Welcome to Download the Newest Braindump2go 70-411 VCE&PDF Dumps: http://www.braindump2go.com/70-411.html (322 Q&As) Do you want to pass Microsoft 70-411 Exam ? If you answered YES, then look no further. Braindump2go offers you the best 70-411 exam questions which cover all core test topics and certification requirements.All REAL questions and answers from Microsoft Exam Center will help you be a 70-411 certified! Exam Code: 70-411
Exam Name Administering Windows Server 2012
Certification Provider: Microsoft
Corresponding Certifications: MCSA, MCSA: Windows Server 2012, MCSE, MCSE: Desktop Infrastructure, MCSE: Private Cloud, MCSE: Server Infrastructure Keywords:70-411 Dumps,70-411 Microsoft Exam Questions,70-411 VCE,70-411 PDF,70-411 Practice Exams,70-411 Practice Tests,70-411 Book,70-411 Study Guide 
QUESTION 81
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource Manager role service installed.
You need to configure Server1 to meet the following requirements:
- Ensure that old files in a folder named Folder1 are archived automatically to a folder named Archive1.
- Ensure that all storage reports are saved to a network share.
Which two nodes should you configure?
To answer, select the appropriate two nodes in the answer area. 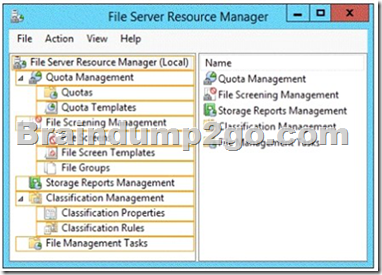
Answer: 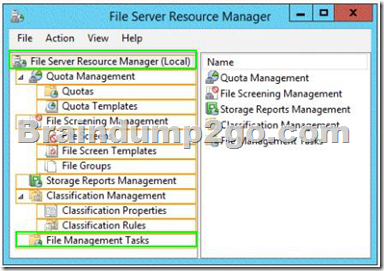
QUESTION 82
Your network contains an Active Directory domain named contoso.com. The domain contains six domain controllers.
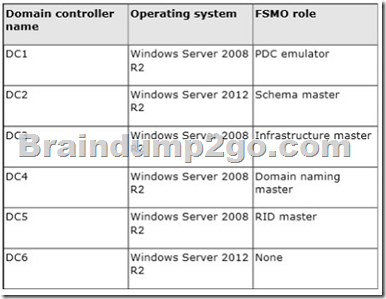
The network contains a server named Server1 that has the Hyper-V server role installed.
DC6 is a virtual machine that is hosted on Server1.
You need to ensure that you can clone DC6.
Which FSMO role should you transfer to DC2? A. Infrastructure Master
B. RID Master
C. Domain Naming Master
D. PDC emulator Answer: D
Explanation:
D. The clone domain controller uses the security context of the source domain controller (the domain controller whose copy it represents) to contact the Windows Server 2012 R2 Primary Domain Controller (PDC) emulator operations master role holder (also known as flexible single master operations, or FSMO). The PDC emulator must be running Windows Server 2012 R2, but it does not have to be running on a hypervisor.
http://technet.microsoft.com/en-us/library/hh831734.aspx QUESTION 83
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed. Server1 hosts 10 virtual machines. A virtual machine named VM1 runs Windows Server 2012 R2 and hosts a processor-intensive application named Appl.
Users report that App1 responds more slowly than expected.
You need to monitor the processor usage on VM1 to identify whether changes must be made to the hardware settings of VM1.
Which performance object should you monitor on Server1? A. Processor
B. Hyper-V Hypervisor Virtual Pcessorro
C. Hyper-V Hypervisor Root Virtual Processor
D. Process
E. Hyper-V Hypervisor Logical Processor Answer: E
Explanation:
In the simplest way of thinking the virtual processor time is cycled across the available logical processors in a round-robin type of fashion. Thus all the processing power gets used over time, and technically nothing ever sits idle.
To accurately measure the processor utilization of a guest operating system, use the
“Hyper-V Hypervisor Logical Processor(_Total)% Total Run Time” performance monitor counter on the Hyper-V host operating system. QUESTION 84
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has the File Server Resource Manager role service installed.
Each time a user receives an access-denied message after attempting to access a folder on Server1, an email notification is sent to a distribution list named DL1.
You create a folder named Folder1 on Server1, and then you configure custom NTFS permissions for Folder1.
You need to ensure that when a user receives an access-denied message while attempting to access Folder1, an email notification is sent to a distribution list named DL2.
The solution must not prevent DL1 from receiving notifications about other access-denied messages.
What should you do? A. From Server Manager, run the New Share Wizard to create a share for Folder1 by selecting the SMB Share - Advanced option.
B. From the File Server Resource Manager console, modify the Access-Denied Assistance settings.
C. From the File Server Resource Manager console, modify the Email Notifications settings.
D. From Server Manager, run the New Share Wizard to create a share for Folder1 by selecting the SMB Share -Applications option. Answer: A
Explanation:
The question states not messing up the notifications to DL1. When creating a second share for a folder, you can define one or more Folder Owner Email addresses on the Management Properties tab when creating the Advanced SMB share.
B: sets global settings regarding , therefore not useable in this situation
C: related to global e-mail settings only (SMTP server, sender address)
D: no option to add Folder Owner Email addresses anywhere QUESTION 85
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains servers named Server1 and Server2. Both servers have the DFS Replication role service installed.
You need to configure the DFS Replication environment to meet the following requirements:
- Increase the quota limit of the staging folder.
- Configure the staging folder cleanup process to provide the highest amount of free space possible.
Which cmdlets should you use to meet each requirement?
To answer, select the appropriate options in the answer area. 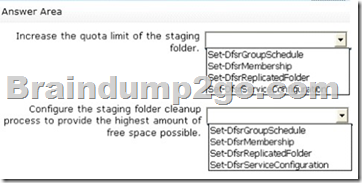
Answer: 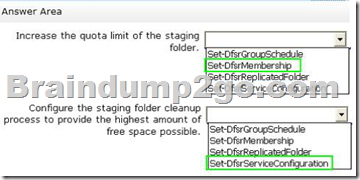
QUESTION 86
Your network contains an Active Directory domain named contoso.com.
You need to create a AD Snapshot.
Which four actions should you perform? To answer, move the four appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Answer: 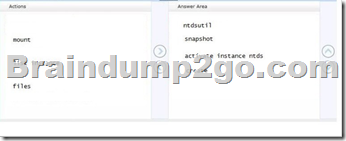
Explanation:
http://www.petri.co.il/working-active-directory-snapshots-windows-server-2008.htm#
http://technet.microsoft.com/en-us/library/cc753609(v=ws.10).aspx QUESTION 87
Your network contains an Active Directory forest named contoso.com. All domain controllers run Windows Server 2008 R2. The schema is upgraded to Windows Server 2012 R2. 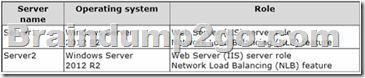
Server 1 and Server2 host a load-balanced application pool named AppPool1.
You need to ensure that AppPool1 uses a group Manged Service Account as its identity.
Which 3 actions should you perform? 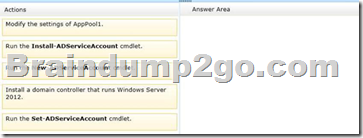
Answer: 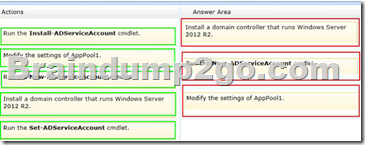
Explanation:
http://technet.microsoft.com/en-us/library/jj128431.aspx QUESTION 88
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. All domain controllers run Windows Server 2012 R2. The domain contains two domain controllers. The domain controllers are configured as shown in the following table. 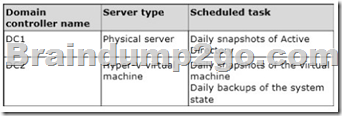
Active Directory Recycle Bin is enabled.
You discover that a support technician accidentally removed 100 users from an Active Directory group named Group1 an hour ago.
What should you do? A. Perform a non-authoritative restore.
B. Modify the is Recycled attribute of Group1.
C. Perform an authoritative restore.
D. Recover the items by using Active Directory Recycle Bin. Answer: C
Explanation:
“You can use three methods to restore deleted user accounts, computer accounts, and security groups. These objects are known collectively as security principals. In all three methods, you authoritatively restore the deleted objects, and then you restore group membership information for the deleted security principals. When you restore a deleted object, you must restore the former values of the member and memberOf attributes in the affected security principal. The three methods are:
Method 1: Restore the deleted user accounts, and then add the restored users back to their groups by using the Ntdsutil.exe command-line tool (Microsoft Windows Server 2003 with Service Pack 1 [SP1] only)
Method 2: Restore the deleted user accounts, and then add the restored users back to their groups
Method 3: Authoritatively restore the deleted user accounts and the deleted users' security groups two times”
http://support.microsoft.com/kb/840001 QUESTION 89
Your network contains an Active Directory domain named contoso.com. The domain contains a read-only domain controller (RODC) named RODC1.
You create a global group named RODC_Admins.
You need to provide the members of RODC_Admins with the ability to manage the hardware and the software on RODC1.
The solution must not provide RODC_Admins with the ability to manage Active Directory objects.
What should you do? A. From Active Directory Users and Computers , configure the Managed By settings of the RODC1 account.
B. From Active Directory Sites and Services, run the Delegation of Control Wizard
C. From Active Directory Users and Computers, run the Delegation of Control Wizard.
D. From a command prompt, run the dsadd computer command. Answer: A
Explanation:
Note:
* You can delegate local administrative permissions for an RODC to any domain user without granting that user any user rights for the domain or other domain controllers. This permits a local branch user to log on to an RODC and perform maintenance work on the server, such as upgrading a driver. However, the branch user cannot log on to any other domain controller or perform any other administrative task in the domain. In this way, the branch user can be delegated the ability to effectively manage the RODC in the branch office without compromising the security of the rest of the domain.
Incorrect:
Not C: The Set-ADAccountControl cmdlet modifies the user account control (UAC) values for an Active Directory user or computer account. UAC values are represented by cmdlet parameters. For example, set the PasswordExpired parameter to change whether an account is expired and to modify the ADS_UF_PASSWORD_EXPIRED UAC value.
Not D: Managed by Tab in Windows Server computer account grantslocal admin access to that RODC. This means he getsControl Access for ResetPassword, and WriteProperty for UserLogonInformation and AccountRestrictions propsets. These allow him to attach an RODC to precreated RODC account, or to perform RODC demotion (with /retainDcMetadata flag). He is also dropped into the local builtin admins group on that RODC QUESTION 90
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. In a remote site, a support technician installs a server named DC10 that runs Windows Server 2012 R2. DC10 is currently a member of a workgroup.
You plan to promote DC10 to a read-only domain controller (RODC).
You need to ensure that a user named Contoso/User1 can promote DC10 to a RODC in the contoso.com domain. The solution must minimize the number of permissions assigned to User1.
What should you do? A. Join DC10 to the domain. Modify the properties of the DC10 computer account
B. From Active Directory Administrative Center, pre-create an RODC computer account.
C. Join DC10 to the domain. Run dsmod and specify the /server switch
D. From Active Directory Administrative Center, modify the security settings of the Domain Controllers
organizational unit (OU). Answer: B
Explanation:
A staged read only domain controller (RODC) installation works in two discrete phases:
1. Staging an unoccupied computer account
2. Attaching an RODC to that account during promotion
Reference: Install a Windows Server 2012 R2 Active Directory Read-Only Domain Controller (RODC)
Braindump2go 70-411 Latest Updaed Braindumps Including All New Added 70-411 Exam Questions from Exam Center which Guarantees You Can 100% Success 70-411 Exam in Your First Try Exam! 
FREE DOWNLOAD: NEW UPDATED 70-411 PDF Dumps & VCE Dumps from Braindump2go: http://www.braindump2go.com/70-411.html (322 Q&As)
|












