[2017-New]Braindump2go 400-251 (PDF & VCE)Exam Dumps 1106Q&As Free Offer[Q86-Q100]
2017 CISCO Official News: 350-018 Exam is Replaced by 400-251 Written Exam Now!
2017 New 400-251: CCIE Security Written Exam v5.1 PDF and VCE Dumps Just Released Today by Braindump2go.com!
1.|2017 NEW 400-251 Written Exam Dumps (PDF & VCE) 1106Q&As Download:
http://www.braindump2go.com/400-251.html
2.|2017 NEW 400-251 Written Exam Questions & Answers:
http://www.braindump2go.com/400-251.html QUESTION 86
Which three statements about the IANA are true? (Choose three.) A. IANA is a department that is operated by the IETF
B. IANA oversees global IP address allocation.
C. IANA managed the root zone in the DNS.
D. IANA is administered by the ICANN.
E. IANA defines URI schemes for use on the Internet. Answer: BCD QUESTION 87
A cloud service provider is designing a large multilenant data center to support thousands of tenants. The provider is concerned about the scalability of the Layer 2 network and providing Layer 2 segmentation to potentially thousands of tenants. Which Layer 2 technology is best suited in this scenario? A. LDP
B. VXLAN
C. VRF
D. Extended VLAN ranges Answer: B QUESTION 88
Refer to the exhibit. Which effect of this configuratioin is true?
 A. The router sends PIM messages only to other routers on the same LAN.
B. The router sends PIM messages, but it rejects any PIM message it receives.
C. The router acts as a stub multicast router for the EIGRP routing protocol.
D. The router accepts all PIM control messages.
E. The router acts as the DR and DF for all bidir-PIM group ranges. Answer: E QUESTION 89
What is the purpose of enabling the IP option selective Drop feature on your network routers? A. To protect the internal network from IP spoofing attacks.
B. To drop IP fragmented packets.
C. To drop packet with a TTL value of Zero.
D. To protect the network from DoS attacks. Answer: D QUESTION 90
Which two answers describe provisions of the SOX Act and its international counterpart Acts? (Choose two.) A. confidentiality and integrity of customer records and credit card information
B. accountability in the event of corporate fraud
C. financial information handled by entities such as banks, and mortgage and insurance brokers
D. assurance of the accuracy of financial records
E. US Federal government information
F. security standards that protect healthcare patient data Answer: BD QUESTION 91
What are two method of preventing DoS attacks on your network? (Choose two) A. Increase the ICMP Unreachable massage rate limit interval.
B. Implement shaping on the perimeter router.
C. Disable the ICMP Unreachable response on the loopback and Null0 interfaces
D. Decrees the ICMP Unreachable massage interval
E. Implement CWBQ on the perimeter router Answer: AE QUESTION 92
What protocol does SMTPS use to secure SMTP connections? A. AES
B. TLS
C. Telnet
D. SSH Answer: B QUESTION 93
Refer to the exhibit, you executed the show crypto key mypubkeyrsa command to verify that the RSA key is protected and it generated the given output.
What command must you have entered to protect the key?
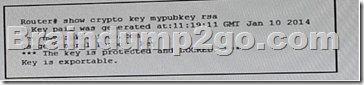 A. crypto key export rsa pki.cisco.com pern url flash: 3des CiscoPKI
B. crypto key decrypt rsa name pki.cisco.com passphrase CiscoPKI
C. crypto key import rsa pki.cisco.com pern url nvram: CiscoPKI
D. crypto key zeroize rsa CiscoPKI
E. crypto key lock rsa name pki.cisco.com passphrase CiscoPKI Answer: E QUESTION 94
All of these Cisco security products provide event correlation capabilities excepts which one? A. Cisco Security MARS
B. Cisco Guard/Detector
C. Cisco ASA adaptive security appliance
D. Cisco IPS
E. Cisco Security Agent. Answer: C QUESTION 95
Refer to the exhibit, which configuration prevents R2 from become a PIM neighbor with R1?
 A. Access-list 10 deny 192.168.1.2.0.0.0.0
!
Interface gi0/0
Ippim neighbor-filter 1
B. Access-list 10 deny 192.168.1.2.0.0.0.0
!
Interface gi0/0
Ipigmp access-group 10
C. Access-list 10 deny 192.168.1.2.0.0.0.0
!
Interface gi0/0
Ippimneighbour-filter 10
D. Access-list 10 permit 192.168.1.2.0.0.0.0
!
Interface gi0/0
Ippim neighbor-filter 10 Answer: D QUESTION 96
Which two certificate enrollment methods can be completed without an RA and require no direct connection to a CA by the end entity? (Choose two.) A. SCEP
B. TFTP
C. manual cut and paste
D. enrollment profile with direct HTTP
E. PKCS#12 import/export Answer: CE QUESTION 97
Which two statements about the MD5 Hash are true? (Choose two.) A. Length of the hash value varies with the length of the message that is being hashed.
B. Every unique message has a unique hash value.
C. Its mathematically possible to find a pair of message that yield the same hash value.
D. MD5 always yields a different value for the same message if repeatedly hashed.
E. The hash value cannot be used to discover the message. Answer: BE QUESTION 98
Which three statement about VRF-Aware Cisco Firewall are true? (Choose three) A. It can run as more than one instance.
B. It supports both global and per-VRF commands and DoS parameters.
C. It can support VPN networks with overlapping address ranges without NAT.
D. It enables service providers to implement firewalls on PE devices.
E. It can generate syslog massages that are visible only to individual VPNs.
F. It enables service providers to deploy firewalls on customer devices. Answer: ADE QUESTION 99
Refer to the exhibit. What is the meaning of the given error message?
 A. The PFS groups are mismatched.
B. The pre-shared keys are mismatched.
C. The mirrored crypto ACLs are mismatched.
D. IKE is disabled on the remote peer. Answer: B QUESTION 100
Which two value must you configure on the cisco ASA firewall to support FQDN ACL ? (Choose two) A. A DNS server
B. A Service policy
C. An FQDN object
D. A Class map
E. A services object
F. A policy map Answer: AC
!!! RECOMMEND!!! 1.|2017 NEW 400-251 Exam Dumps (PDF & VCE) 1106Q&As Download:
http://www.braindump2go.com/400-251.html
2.|2017 NEW 400-251 Study Guide Video:
YouTube Video: YouTube.com/watch?v=GSXnXKIh834 2 1
" href="https://youtu.be/GSXnXKIh834"> YouTube Video: YouTube.com/watch?v=GSXnXKIh834 2 1
|



