2016 Latest Braindump2go 70-663 Exam Questions PDF Free Download (61-70)
MICROSOFT NEWS: 70-663 Exam Questions has been Updated Today! Get Latest 70-663 VCE and 70-663 PDF Instantly! Welcome to Download the Newest Braindump2go 70-663 VCE&70-663 PDF Dumps: http://www.braindump2go.com/70-663.html (291 Q&As) 70-663 Exam Dumps are recently new updated by Microsoft Official! Braindump2go also updates all the 70-663 Exam Questions and now all the 291q are the latest(add many new questions this time)! Braindump2go is famous for our AMAZING 99.6% exam pass rate. Join our success! Then you can pass 70-663 Exam successfully under our professional help! We guarantee! Exam Code: 70-663
Exam Name: Pro: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
Certification Provider: Microsoft
Corresponding Certifications: MCITP, MCITP: Enterprise Messaging Administrator on Exchange 2010 70-663 Dumps,70-663 Dumps PDF,70-663 Dumps VCE,70-663 PDF,70-663 VCE,70-663 Study Guide,70-663 Braindump,70-663 Book,70-663 Exam Questions,70-663 Practice Test,70-663 Practice Exam,70-663 eBook,70-663 Preparation 
QUESTION 61
You have an Exchange Server 2010 organization.
Your company acquires two companies named Contoso, Ltd and Northwind Traders.
You need to ensure that users from Contoso have only contoso.com e-mail addresses and users from Northwind Traders have only traders.com e-mail addresses.
What should you create and configure? A. two accepted domains and two e-mail address policies
B. two remote domains and two accepted domains
C. two transport rules and two address remote entries
D. two Receive connectors and two address lists Answer: A
Explanation:
E-mail address policies generate the primary and secondary e-mail addresses for your recipients so they can receive and send e-mail.
This default policy specifies the recipient's alias as the local part of the e-mail address and uses the default accepted domain.
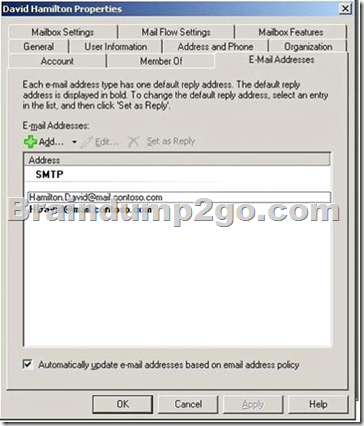
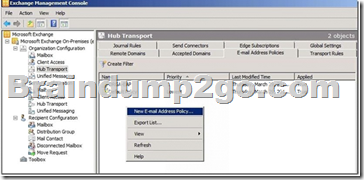
If you want to specify additional e-mail addresses for all recipients or just a subset, you can modify the default policy or create additional policies.
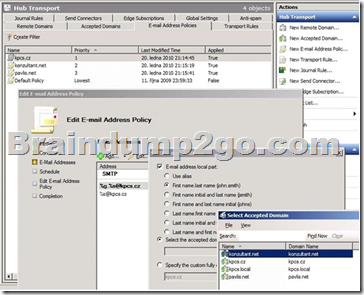
When creating a new address policy you select from the list of accepted domains:
 QUESTION 62
You have an Exchange Server 2010 organization.
You plan to deploy a database availability group (DAG).
You need to recommend disk configuration for the servers in the organization.
The solution must minimize costs.
What should you recommend? A. 7200 RPM SATA hard disks in a Direct Attach Storage (DAS)
B. 7200 RPM SATA hard disks in a Network Attached Storage (NAS)
C. 15000 RPM SAS hard disks in a Network Attached Storage (NAS)
D. 15000 RPM SAS hard disks in a Fiber Channel (FC) Storage Area Network (SAN) Answer: A
Explanation:
Microsoft recommends DAS [for example JBOD on SATA] when Mailbox server is not virtualized. But there are scalability problems. You would need to have at least capacity for 2 years period.
Another alternative is iSCSI SAN.
And finaly Fibre channel SAN. D is expensive.
Exchange 2010 doesn't support network-attached storage (NAS).
For Exchange Server 2010, the IOPS per user is now 0.1 (it was 0.3 IOPS per user in 2007) [in Exchange 2010 ESE combines multiple I/O operation into a single request].
therefore in theory you could have:

It is better to have large disk but slower disk: a 1TB disk that can perform only 50 IO operations per second (IOPS) can provide substantially more capacity than the 146GB disk at only 25 percent of the cost.
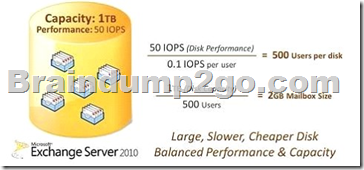
The combination of JBOD and less expensive disks can result in dramatic cost savings for your organization. QUESTION 63
You have an Exchange Server 2007 organization.
All users connect to mailboxes by using Microsoft Office Outlook 2003.
You plan to transition the organization to Exchange Server 2010.
You need to recommend a solution for mailbox access that meets the following requirements:
- Minimize support costs
- Minimize software costs
- Provide access to Public folders
What should you recommend? A. Implement POP3 and IMAP4 access
B. Implement Personal Archive and forms-based authentication
C. Implement Autodiscover and upgrade all client computers to Outlook 2010
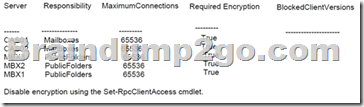
D. Implement Outlook Anywhere and modify the Outlook RPC encryption settings Answer: D
Explanation:
If you use Outlook 2003 with Exchange Server 2010 you must disable RPC encryption on the CAS Servers.
[PS] C:Windowssystem32>Get-RpcClientAccess
There are three main tasks to deploy Outlook Anywhere in an Exchange environment:
Enable and configure Outlook Anywhere on the Client Access server Configure the perimeter firewall to allow SSL/HTTPS connections from external networks to the Client Access server Configure the Outlook clients to use Outlook Anywhere when connecting from remote networks
 QUESTION 64
Your network contains two data centers named Datacenter1 and Datacenter2.
An Active Directory site exists for each data center.
The data centers connect to the Internet by using a direct link.
The data centers connect to each other by using a high speed WAN link.
You plan to deploy Exchange Server 2010 Mailbox servers in both data centers.
You need to plan message routing to meet the following requirements:
- Ensure outbound delivery of e-mail messages if a single server fails
- Automatically load balance the Hub Transport server in each site
- Deploy the minimum number of servers
What should you include in the plan? A. In each data center, deploy one Hub Transport server.
Create and configure one Send connector.
B. In each data center, deploy two Hub Transport servers.
Create and configure one Send connector.
C. In each data center, deploy one Edge Transport server.
Create and configure two Send connectors.
D. In each data center, deploy two Edge Transport servers.
Create and configure two Send connectors. Answer: B QUESTION 65
You have an Exchange organization that contains Exchange 2000 Server Service Pack 3 (SP3), Exchange Server 2003 Service Pack 2 (SP2) and Exchange Server 2007 Service Pack 1 (SP1) servers.
You need to transition the organization to Exchange Server 2010.
What should you do first? A. Remove all Exchange Server 2007 SP1 servers from the organization.
B. Remove all Exchange 2000 Server and all Exchange Server 2003 servers from the
organization.
C. Remove all Exchange 2000 Server servers from the organization and then upgrade all
Exchange Server 2007 servers to SP2.
D. Remove all Exchange Server 2003 servers from the organization and then upgrade all
Exchange Server 2007 servers to SP2. Answer: C
Explanation:
Upgrade existing Exchange 2003 servers to Exchange 2003 Service Pack 2 (SP2).
Upgrade existing Exchange 2007 servers to Exchange 2007 Service Pack 2 (SP2).
QUESTION 66
You have an Exchange Server 2010 organization.
You plan to deploy a public folder access solution that meets the following requirements:
- Users in the legal department must be able read e-mail sent to public folders
- Users in the legal department must not be able to post documents to public folders by using Outlook Web App (OWA)
You need to recommend modification to the organization to meet the requirements of the public folder access solution.
What should you recommend? A. Modify the mailbox permissions.
B. Modify the OWA segmentation settings.
C. Modify the public folder client permissions.
D. Modify the public folder administrative permissions. Answer: C
Explanation:
Each public folder has two sets of permissions: client permissions and admin permissions. If you are using Outlook or Outlook Web Access to access a public folder, we only look at the client permissions.
Client permissions are the ones you see when you get properties on a folder in Outlook, or when you use the Get-PublicFolderClientPermission cmdlet, or when you look at Folder Permissions in the ExFolders or PFDAVAdmin tool.
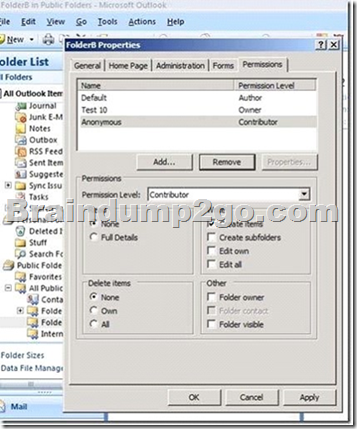
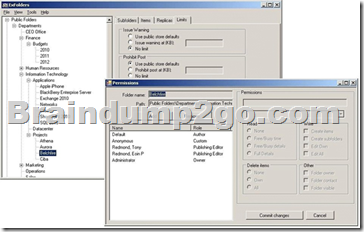 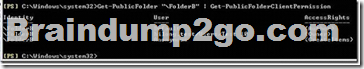
Since folders in the hierarchy have typically been created by many different users, the client permissions are often different on each folder. The creator of the folder will be the Owner, and will often change the other rights on the folder as well, so there's no telling what the client permissions will look like throughout the hierarchy.
OWA Segmentation settings can only allow or prevent access to PF. Detailed permissions are controlled with client settings:
QUESTION 67
Your company has an Exchange Server 2010 organization.
The company's compliance policy states that all e-mail messages older than three months must be deleted automatically.
You need to recommend a solution to prevent the deletion of e-mail for users on extended leave. The solution must ensure that users can view of their e-mail when they return to work.
What should you recommend? A. a legal hold
B. a retention hold
C. an Outlook Protection Rule
D. an Transport Protection Rule Answer: B
Explanation:
Placing a mailbox on retention hold suspends the processing of a retention policy or managed folder mailbox policy for that mailbox.
Retention hold is designed for scenarios such as a user being on vacation or away temporarily.
Controlled through the Messaging Records Management:
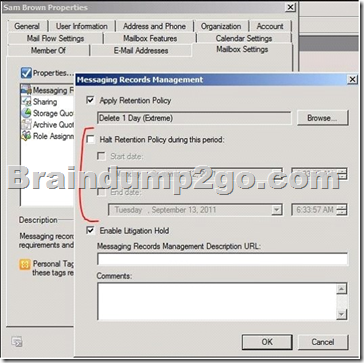
During retention hold, users can log on to their mailbox and change or delete items.
When you perform a mailbox search, deleted items that are past the deleted item retention period aren't returned in search results.
To make sure items changed or deleted by users are preserved in legal hold scenarios, you must place a mailbox on legal hold. For more information, see Place a Mailbox on Litigation Hold.
You can also include retention comments for mailboxes you place on retention hold.
The comments are displayed in supported versions of Microsoft Outlook. http://technet.microsoft.com/en-us/library/dd335168.aspx QUESTION 68
Your network contains an internal network and a perimeter network.
The perimeter network contains an Exchange Server 2010 Edge Transport server.
You need to recommend a remote management solution for the Edge Transport server that meets the following requirements:
- All management traffic must be encrypted
- The solution must allow remote administration from the internet network
- The solution must support the use of the Exchange Management Console (EMC)
What should you recommend? A. Lightweight Directory Access Protocol (LDAP) over Secure Socket Layer (SSL).
B. Remote Desktop Protocol (RDP) over Secure Socket Layer (SSL).
C. Windows Management Instrumentation Command-line (WMIC)
D. Windows Remote Management (WinRM) over SSL Answer: B
Explanation:
Since solution must support EMC you need to login to the server.
The only way to connect from the internet is by RDP.
WinRM will be most likely restricted.
The question is talking about EMC not EMS
Top five ways to avoid driving to the office in the middle of the night:
1. Exchange Management Console
The Exchange Management Console (EMC) is one method to manage your Exchange Server as it is now remote-capable. You essentially run a local version of EMC on your workstation and connect to a remote Exchange Server in order to manage it. It is important to note that a 64-bit host system is required, as that the EMC only runs on 64-bit system. In addition, for security reasons, only the Edge Transport server role appears for servers that have the Edge Transport server role installed ?regardless of any other server roles that may be present.
2. Remote Exchange Management Shell
Exchange Server cmdlets can be remotely accessed via Exchange Manage Shell (EMS) using the PowerShell scripting language. This feature is new to Exchange Server 2010, and is powerful as it allows multiple servers to be managed as a single EMS instance from a remote workstation. The EMS is more powerful for certain tasks and also has the advantage of not being subjected to the requirement of a 64-bit host system. Organizations that have deployed Office 365 will be interested to know that EMS works with Exchange Online too.
3. Exchange Control Panel
Also introduced in Exchange Server 2010, the Exchange Control Panel (ECP) allows an administrator to remotely configure specific aspects of Exchange Server with nothing more than a supported web browser.
Accessed from the http://<servername>/ECP URL, ECP functions through the firewall and is similar to accessing the Outlook Web App. Mailboxes can be managed from the ECP, including distribution groups, contacts, as well as other objects such as journaling and transport rules. While not as comprehensive as some of the available other administrative options, it does at least make quick tweaks possible with a minimum of fuss.
4. Remote Desktop Protocol
RDP, or Remote Desktop Protocol, is one of the most common protocols for remote access to Exchange Server, as well as Windows Servers in general. RDP is popular as it is commonly understood, fast and generally considered to be a secure method for remote administration. There are two options to bear in mind here from a licensing perspective:
Remote Desktop for Administration and Terminal Services. The first is limited to two connections and incurs no additional licensing costs. The latter has a greater amount of versatility, but has an added cost overhead.
5. IP-based KVM
IP-based KVM (Keyboard-Video-Mouse) appliances do not utilize made-in-Microsoft technologies. These are used to wire-up anything from a single server, to hundreds of them, by connecting to their video, keyboard and mouse ports for remote management over the LAN or Internet. One advantage of using an IP-based KVM solution would be that it is not limited to Exchange Servers, but can be used for general server maintenance tasks. Moreover, companies whose servers are located in hard-to-access server closets, or data center locations, may already have an IP-KVM in place for managing them. QUESTION 69
Your network contains two Active Directory site.
The sites connect to each other by using a WAN link.
You plan to deploy two Exchange Server 2010 Mailbox servers and two Client Access servers in each site.
Each site will contain a Client Access array.
You need to recommend a solution to deploy Hub Transport servers.
The solution must meet the following requirements:
- Continue to deliver e-mail messages to users in other sites if a single Hun Transport server fails
- Support the planned Client Access array deployment
- Minimize the number of Exchange servers
What are two possible ways to achieve this goal? (Each answer presents a complete solution. Choose two.) A. Add the Hub Transport server role to each Mailbox server.
B. Add the Hub Transport server role to each Client Access server.
C. Deploy two Hub Transport servers on two new servers in each site.
D. Deploy one Hub Transport server on a new server and then install the SMTP service on
each Client Access server. Answer: AB
Explanation:
To minimize number of servers Hub transport can be combined with CAS or Mailbox server. QUESTION 70
You have an Exchange Server 2010 organization.
An Edge Transport server sends and receives all e-mail messages
You notice that some servers on the Internet identify e-mail messages from your organization as spam.
You need to minimize the possibility that e-mail messages send from your organization are identified as spam.
What should you do? A. Implement Microsoft Forehead Security for Exchange Server.
B. Create SenderID TXT records for the Edge Transport servers.
C. Configure the Edge Transport servers to use a real-time block list (RBL).
D. Install a server certificate from a trusted third-party certification authority (CA). Answer: B
Explanation:
In Exchange 2010, Sender ID makes spoofing more difficult. When you enable Sender ID, each message contains a Sender ID status in the metadata of the message. When an e- mail message is received, the Edge Transport server queries the sender's DNS server to verify that the IP address from which the message was received is authorized to send messages for the domain that's specified in the message headers. The IP address of the authorized sending server is referred to as the purported responsible address (PRA).
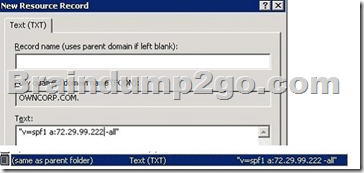
SPF records identify authorized outbound e-mail servers. If an SPF record is configured on the sender's DNS server, the Edge Transport server parses the SPF record and determines whether the IP address from which the message was received is authorized to send e-mail on behalf of the domain that's specified in the message.

The Edge Transport server updates the message metadata with the Sender ID status based on the SPF record. After the Edge Transport server updates the message metadata, the Edge Transport server delivers the message as it ordinarily would.
http://technet.microsoft.com/en-us/library/aa996295.aspx
Instant Download Braindump2go New Released Microsoft 70-663 Exam Dumps PDF & VCE! Enjoy 1 year Free Updation! 100% Exam Pass Guaranteed Or Full Money Back! 
FREE DOWNLOAD: NEW UPDATED 70-663 PDF Dumps &70-663 VCE Dumps from Braindump2go: http://www.braindump2go.com/70-663.html (291 Q&As)
|



















