(14th/11/2017 New)100% Exam Pass-70-697 PDF and VCE Free from Braindump2go(56-66)
2017 Novmber New 70-697 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 70-697 Questions:
1.|2017 New 70-697 Exam Dumps (PDF & VCE) 215Q&As Download:
https://www.braindump2go.com/70-697.html 2.|2017 New 70-697 Exam Questions & Answers Download:
https://drive.google.com/drive/folders/0B75b5xYLjSSNUnFOeVNOSmo1VlE?usp=sharing QUESTION 56
Group Policy is a set of rules which control the working environment of user accounts and computer accounts. Group Policy provides the centralized management and configuration of operating systems, applications and users' settings in an Active Directory environment.
In other words, Group Policy in part controls what users can and can't do on a computer system.
Which one of these policies requires a reboot? A. Turn off Windows Defender
B. Turn off Autoplay for non-volume devices
C. Disable Active Desktop
D. Turn off Data Execution Prevention for Explorer Answer: D
Explanation:
You can Turn Off Windows Defender anytime (Uninstalling it is another thing!) without rebooting.
A reboot is REQUIRED when turning off DEP for Explorer. QUESTION 57
Which term is used to refer to installing apps directly to a device without going through the Windows Store? A. SQL Injection
B. BranchCache
C. DLL Hijack
D. Sideloading Answer: D QUESTION 58
IPv6 has a vastly larger address space than IPv4.
This expansion provides flexibility in allocating addresses and routing traffic and eliminates the primary need for network address translation (NAT).
Do you know how many more bits there are in an IPv4 address compared to an IPv6 address? A. 4 times more
B. 6 times more
C. Twice as many
D. 8 times more Answer: A
Explanation:
IPv4 addresses are 32 bit, IPv6 addresses are 128 bit. QUESTION 59
You are using sysprep to prepare a system for imaging.
You want to enable end users to customize their Windows operating system, create user accounts, name the computer, and other tasks.
Which sysprep setting should you use? A. /oobe
B. /audit
C. /generalize
D. /unattend Answer: A
Explanation:
The /oobe option restarts the computer into Windows Welcome mode. Windows Welcome enables end users to customize their Windows operating system, create user accounts, name the computer, and other tasks. Any settings in theoobeSystem configuration pass in an answer file are processed immediately before Windows Welcome starts. QUESTION 60
You have set up a new wireless network for one of your prestigious clients.
The director wants to ensure that only certain designated wireless laptops can connect to the new network to prevent misuse.
What do you need to do? A. Use MAC address control
B. Use IPv4 address control
C. Use WEP
D. Use WPA Answer: A
Explanation:
Media Access Control address (MAC address) is a unique identifier assigned to most network adapters or network interface cards (NICs) by the manufacturer for identification, and used in the Media Access Control protocol sub-layer. If assigned by the manufacturer, a MAC address usually encodes the manufacturer's registered identification number. It may also be known as an Ethernet Hardware Address (EHA), hardware address, adapter address, or physical address. QUESTION 61
Drag and Drop Questions
You support desktop computers for a company named Fabrikam, Inc.
The computers are members of the Active Directory domain named fabrikam.com.
Fabrikam works with a supplier named Contoso, Ltd.
Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain.
The website requires SSL and mutual authentication.
You need to configure the computers to allow Fabrikam users to access the Contoso website without any warning prompts.
You also need to use the fewest certificates possible.
Which certificate or certificates should you use? (To answer, drag the appropriate certificate to the correct certificate store. Each certificate may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Answer:
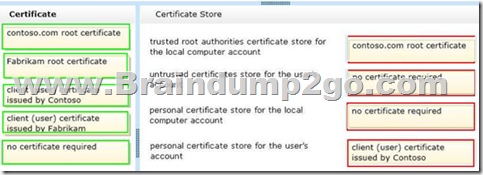
Explanation:
Note:
- contoso.com provided the resources. contoso.com be the trusted root authorities store
- No untrusted certificates
- Not allow access to local computer account (just to user account)
- user account access through client (user) certificate issued by Contoso QUESTION 62
You administer computers that run Windows 8 Pro and are members of an Active Directory domain.
The computers are encrypted with BitLocker and are configured to store BitLocker encryption passwords in Active Directory. A user reports that he has forgotten the BitLocker encryption password for volume E on his computer.
You need to provide the user a BitLocker recovery key to unlock the protected volume.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.) A. Ask the user for his computer name.
B. Ask the user to run the manage-bde-unlock E:-pw command.
C. Ask the user for his logon name.
D. Ask the user for a recovery key ID for the protected volume. Answer: AD
Explanation:
(1) Saying a name does not verify you at all. You can easily find out the name of the owner if you have the access to the PC. For example, open Outlook or simply press Start to verify username. In such cases mobile phone call verification would is preferred, but it is not mentioned in the answers.
(2) It is mentioned in the conditions, that some (NOT ONE) volumes on the computers are encrypted. This means you will have to find out which is locked. So you need recovery key ID.
http://www.concurrency.com/blog/enable-bitlocker-automatically-save-keys-to-active-directory/ QUESTION 63
You have a desktop computer that runs Windows 8 Enterprise.
You add three new 3-terabyte disks.
You need to create a new 9-terabyte volume.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.) A. From Disk Management, create a new spanned volume.
B. From Disk Management, convert all of the 3-terabyte disks to GPT.
C. From PowerShell, run the New-VirtualDisk cmdlet.
D. From Disk Management, bring all disks offline.
E. From Diskpart, run the Convert MBR command.
F. From PowerShell, run the Add-PhysicalDisk cmdlet. Answer: AB
Explanation:
Create a Spanned Volume
A spanned volume is a dynamic volume consisting of disk space on more than one physical disk. If a simple volume is not a system volume or boot volume, you can extend it across additional disks to create a spanned volume, or you can create a spanned volume in unallocated space on a dynamic disk.
http://technet.microsoft.com/en-us/library/cc772180.aspx
To create a spanned volume using the Windows interface
1. In Disk Management, right click the unallocated space on one of the dynamic disks where you want to create the spanned volume.
2. Click New Spanned Volume.
3. Follow the instructions on your screen.Using GPT Drives
http://msdn.microsoft.com/en-us/library/windows/hardware/gg463524.aspx
A GPT disk uses the GUID partition table (GPT) disk partitioning system.
A GPT disk offers these benefits:
Allows up to 128 primary partitions.
Master Boot Record (MBR) disks can support up to four primary partitions and an additional 124 partitions inside extended partitions.
Allows a much larger partition size-greater than 2 terabytes (TB), which is the limit for MBR disks.
Provides greater reliability because of replication and cyclical redundancy check (CRC) protection of the partition table. Can be used as a storage volume on all x64-based platforms, including platforms running Windows XP Professional x64 Edition.
Starting with Windows Server 2003 SP1, GPT disks can also be used as a storage volume on x86-based Windows platforms.Can be used as a boot volume on x64-based editions of Windows 7, Windows Vista, and Windows Server 2008.
Starting with Windows Server 2003 SP1, GPT disks can also be used as a boot volume on Itanium-based systems.
Note: Windows only supports booting from a GPT disk on systems that contain Unified Extensible Firmware Interface (UEFI) boot firmware. QUESTION 64
A company has a main office located in Miami, and brach offices in Boston, Los Angeles and Portland.
The Office Networks are configured as described in the following table.
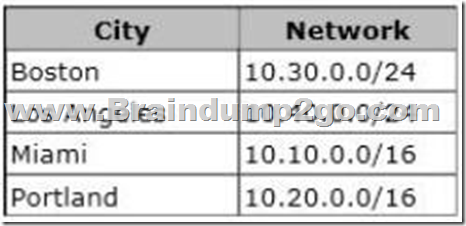
A management computer in the main office, named COMPUTER1, runs windows 8 and several third-party management applications.
- Ensure that only users in the Boston office can connect to COMPUTER1 by using http.
- Ensure that only users in the Los Angeles office can connect COMPUTER1 by using https
- Ensure that only users in th Portland office can connect to COMPUTER1 by using FTP.
You are configuring access to COMPUTER1.
How should you configure windows firewall? (To answer, drag the appropriate elements to the correct location or locations in the answer area. Elements may be used once, more than once, or not at all. You ma need to drag the split bar between panes or scroll.)
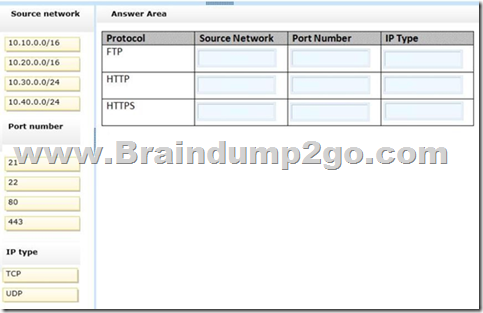
Answer:

Explanation:
Seems to be TCP on every answer.
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers QUESTION 65
Drag and Drop Question
You administer Windows 8.1 Enterprise computers.
Your company has a team of technical writers that is preparing technical manuals and help files. The team manager wants to ensure that the technical writers are able to restore any documents that been modified within the last year.
You need to ensure that the technical writers can restore Microsoft Word files to any previous versions for up to one year.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)

Answer:
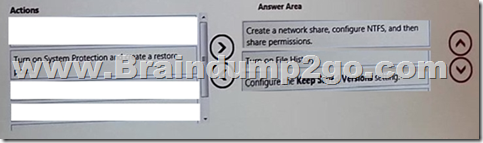
Explanation:
https://www.winhelp.us/file-history-in-windows-8.html QUESTION 66
Drag and Drop Question
You manage update compliance for Windows 8.1 desktop computers that are part of a domain.
You need to configure new desktops to automatically receive updates from an intranet resource that you manage.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
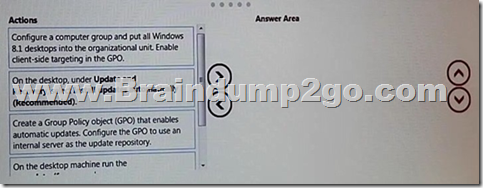
Answer:
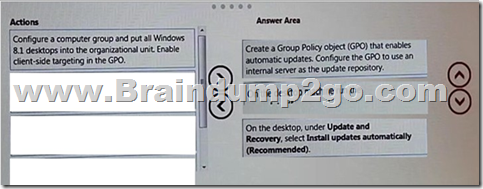
Explanation:
Box 1: Create a GPO that enables automatic updates through the intranet source.
Box 2: gpupdate /force
The Gpupdate command refreshes local andActive Directory-based Group Policy settings, including security settings. The /force Ignores all processing optimizations and reapplies all settings.
Box 3: Configure the clients to install updates automatically.
Incorrect Answers:
* Client side targeting
With client-side targeting, you enable client-computers to add themselves to the computer groups you create in the WSUS console.
https://technet.microsoft.com/en-us/library/bb490983.aspx
!!!RECOMMEND!!!
1.|2017 New 70-697 Exam Dumps (PDF & VCE) 215Q&As Download:
https://www.braindump2go.com/70-697.html2.|2017 New 70-697 Study Guide Video:
YouTube Video: YouTube.com/watch?v=lvar3kxnfo4
|








